Mask data using Attribute-Based Access Control (ABAC)
This article shows step-by-step of how to mask sensitive data such as PII (Personal Identifiable Information) in Pega application using Attribute-Based Access Control (ABAC) security model in Pega Platform. (For how to encrypt data using ABAC, read this article.)
===
Configurations
Step 1 - Optimize SSN property in the work class; i.e. expose the column in the DB table.
Step 2 - Create an Access Control Policy rule in the work class with Action=PropertyRead.
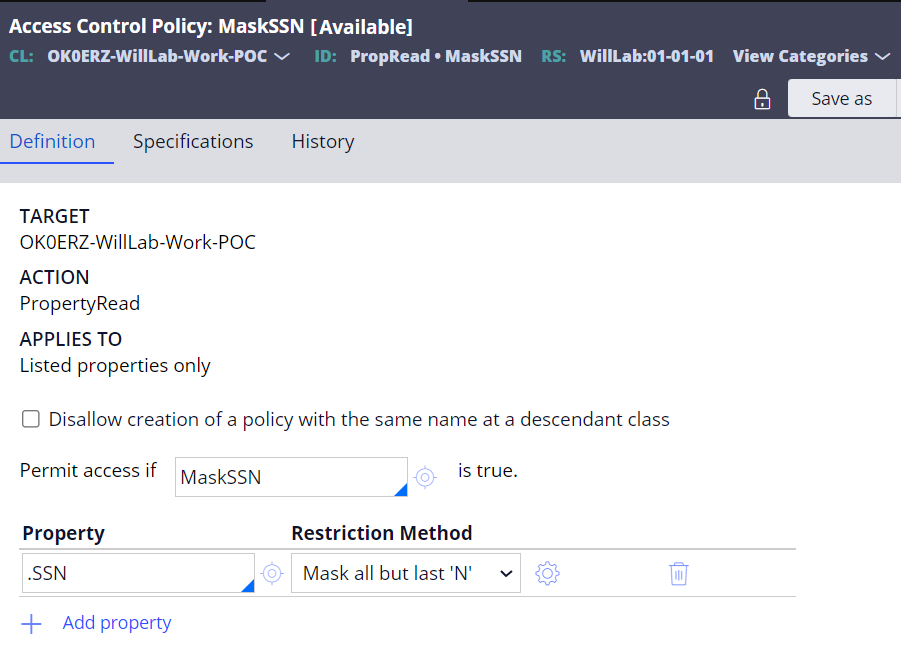
Step 3 - Create Access Control Policy Condition rule.
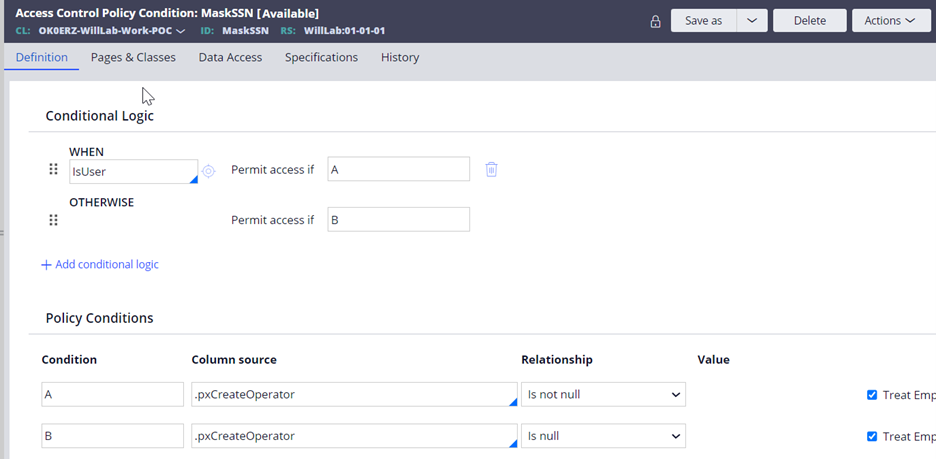
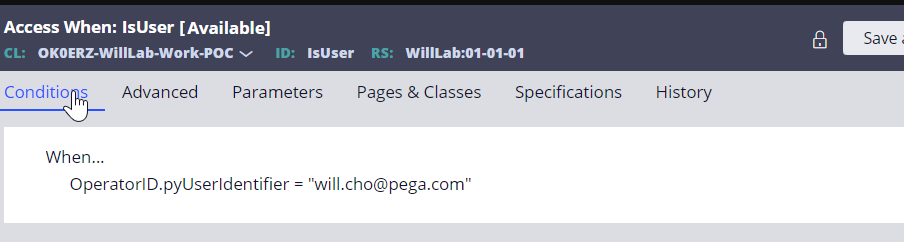
Step 4 - Create Access When rule.
a. Only [email protected] Operator ID can see the SSN value, which will be masked for other Operator IDs.
Step 5 - Run and verify the result.
a. Result 1 (UI)
When [email protected] opens the case, it’s masked.
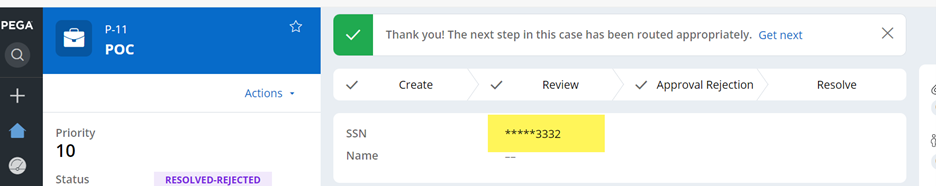
Only [email protected] is permitted to see as configured in the access when rule.
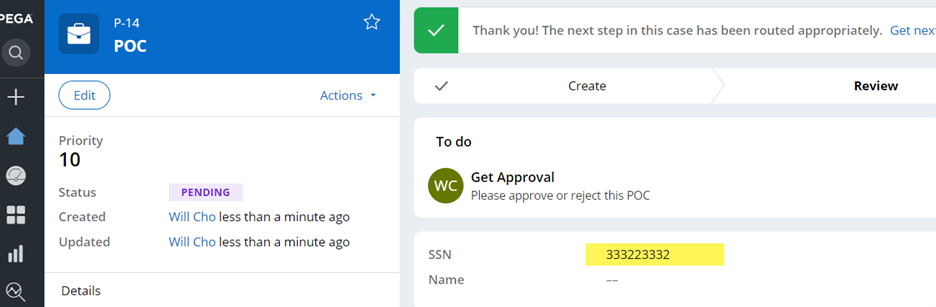
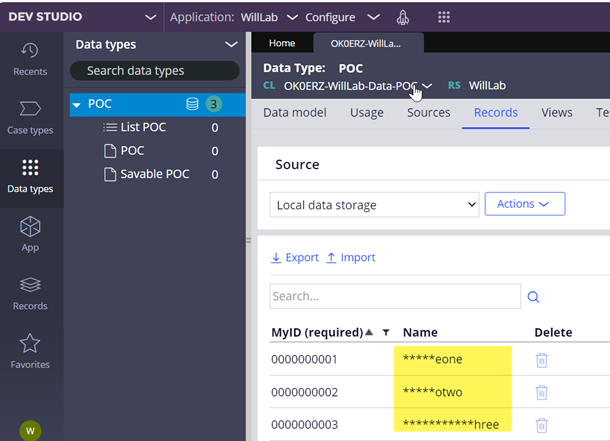
b. Result 2 (data type table)
View from [email protected] (masked):
View from will.cho@pega (unmasked):
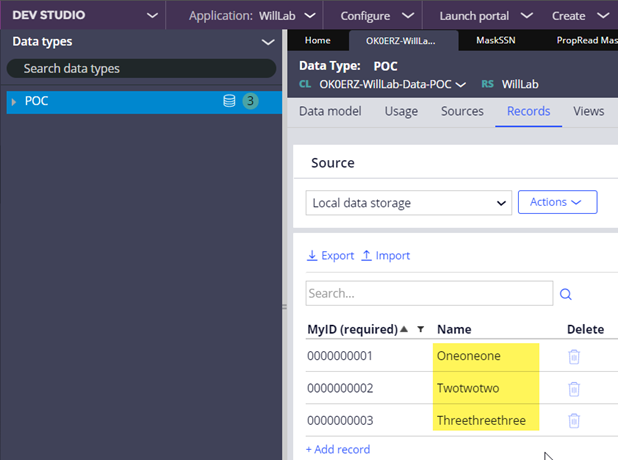
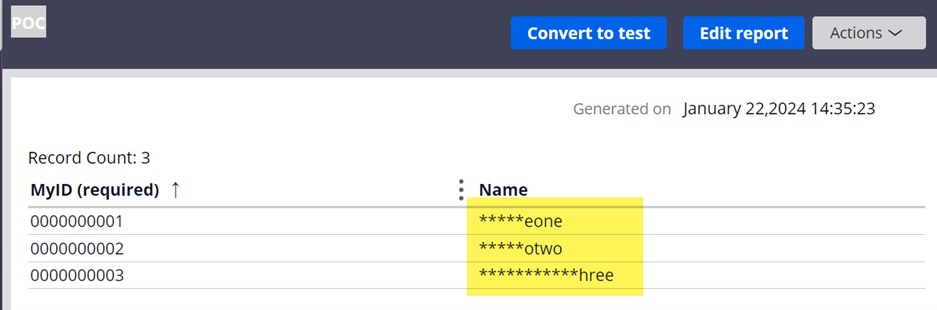
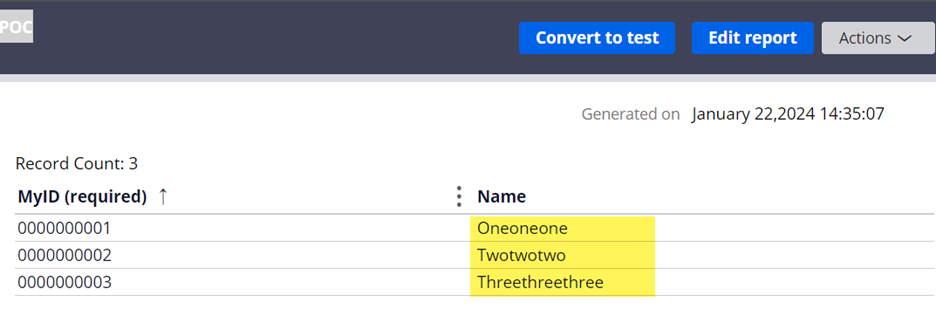
c. Result 3 (report definition)
View from [email protected] (masked):
View from [email protected] (unmasked):
= = =
In addition, the access control policy (Action=PropertyRead) works for an embedded property.
The following Table layout is sourced from pyWorkPage.MyList() pagelist property.
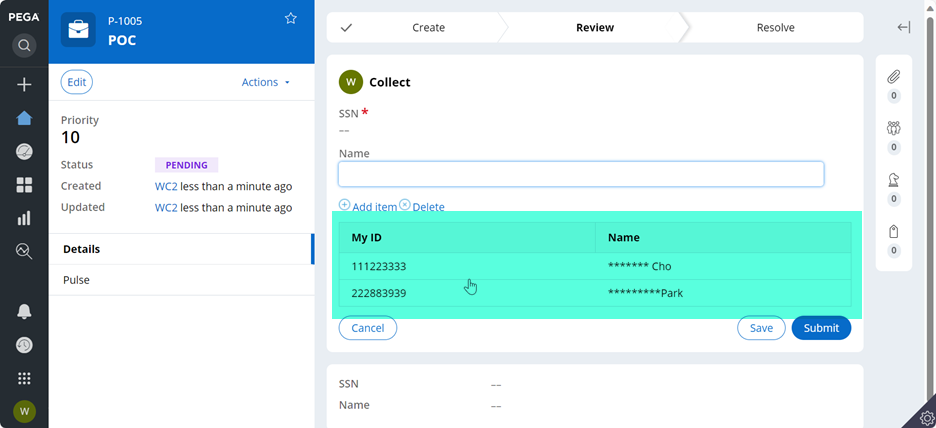
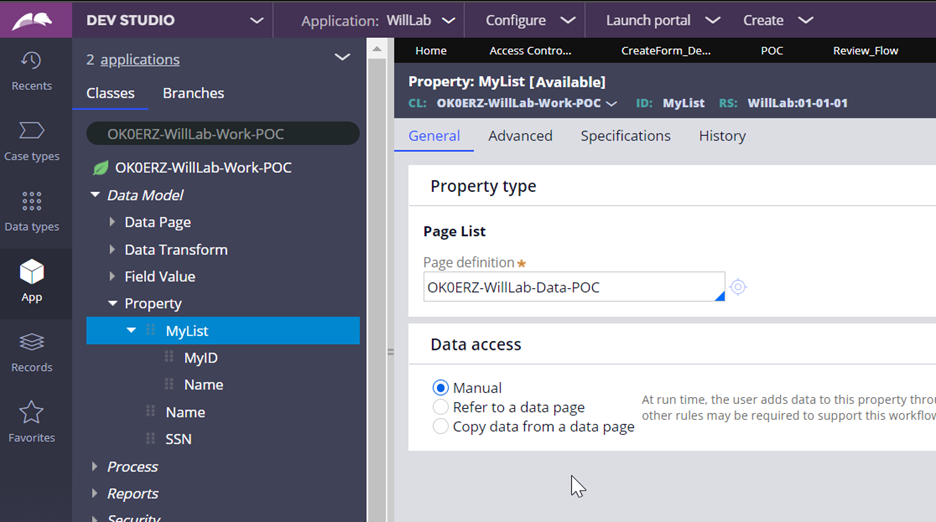
Here is the pagelist property definition.
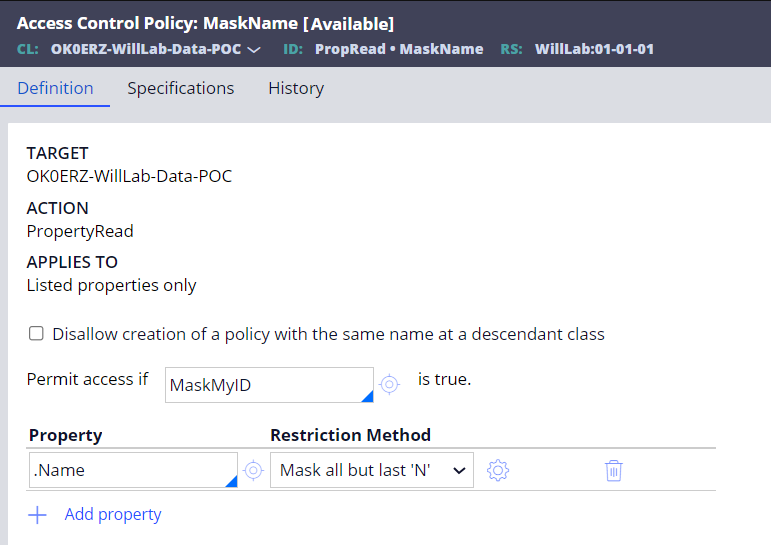
The following access control policy rule is created in the data class used as a definition of the pagelist. We added .Name property for masking.
Please leave any question or feedback.
===
Other reference - How to "encrypt" sensitive data using Attribute-Based Access Control (ABAC) in Pega

@Will Cho This article you've published is really helpful, thanks for that. Is there a way to mask the info using a custom Restriction Method for text rather than the three options Pega gives us (full maks, first 'N', last 'N')? For example, something like this:
NNNNNN******NNNN