Is there a simple way to verify that the authentication profile is correctly configured?
In the last month we are adopting the OAuth 2.0 mechanism to authenticate Pega towards the other systems and for that we are using an Authentication Profiles configured for Keycloak as in the following image
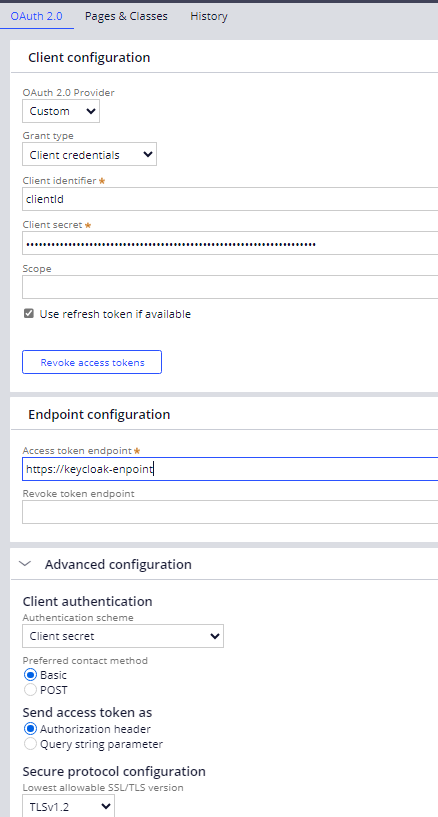
The big issue that we had in all the environment was testing the connection and in particular the authentication towards Keycloak (check if the clientid and the password are correct). In fact we were not able to effectively debug the authentication problems, i.e. if the authentication error was sent to us by keyclock or by the external system.
Is there a way to easily DEBUG these situations?
Is there a simple way to check the authentication of Pega towards Keycloak?
