Question
Pegasystems Inc.
AU
Last activity: 16 Oct 2018 12:03 EDT
We are getting the following error while invoking the REST connector:****javax.net.ssl.SSLPeerUnverifiedException: peer not authenticated
We are getting the following error while invoking the REST connector:****javax.net.ssl.SSLPeerUnverifiedException: peer not authenticated.
When we tried to trace the error, it showed that there is an error in Step-12 of the activity pyInvokeRestConnector, so we put debugging steps in the java code being called in that step.
We found that the error is thrown on execution of this java code snippet:-
// ** httpResponse = client.execute(httpRequest, (com.pega.apache.http.protocol.BasicHttpContext)localContext) **//
Please advise what can be the issue.
Please note that this feature was working in lower environments.
**Moderation Team has archived post**
This post has been archived for educational purposes. Contents and links will no longer be updated. If you have the same/similar question, please write a new post.
-
Like (0)
-
Share this page Facebook Twitter LinkedIn Email Copying... Copied!
Pegasystems Inc.
US
Hi Nishant,
Check out the following PDN SA and see if it helps.
https://community.pega.com/support/support-articles/restful-services-fail-sslpeerunverifiedexception
~Ankur
Pegasystems Inc.
IN
Hi Nishant,
In Pega7 Security improvements were made to Connect-REST rules so that it runs under a SecurityManager and SSLSocketFactory from within the Pega application and not resorting to the underlying JDK’s SecurityManager and SSLSocketFactory.
Refer the below link and try the solution suggested.
Regards,
Sudhish OP
Pegasystems Inc.
GB
Sounds like the REST endpoint you are connecting to is presenting a Certificate that is not trusted by your PRPC system (or possibly [rarer] it is requesting that your REST call present it's own Client Certificate [two-way SSL]).
First find out if you are using TWO-WAY SSL (because that involves more steps); if you are not and are just using ONE-WAY SSL; then see below for a general approach about what you probably need to do here.
SUGGESTED STEPS:
1. Use 'openssl' to retrieve the certificate used by the endpoint.
Like this:
openssl s_client -connect www.google.com:443 -showcerts
If you look through the output, you'll see at least one Certificate (base64 encoded, PEM format); so in the example above; I get this Certificate (actually I get three in total - but here's the last one in the list for illustration):
Sounds like the REST endpoint you are connecting to is presenting a Certificate that is not trusted by your PRPC system (or possibly [rarer] it is requesting that your REST call present it's own Client Certificate [two-way SSL]).
First find out if you are using TWO-WAY SSL (because that involves more steps); if you are not and are just using ONE-WAY SSL; then see below for a general approach about what you probably need to do here.
SUGGESTED STEPS:
1. Use 'openssl' to retrieve the certificate used by the endpoint.
Like this:
openssl s_client -connect www.google.com:443 -showcerts
If you look through the output, you'll see at least one Certificate (base64 encoded, PEM format); so in the example above; I get this Certificate (actually I get three in total - but here's the last one in the list for illustration):
-----BEGIN CERTIFICATE-----
MIIDfTCCAuagAwIBAgIDErvmMA0GCSqGSIb3DQEBBQUAME4xCzAJBgNVBAYTAlVT
MRAwDgYDVQQKEwdFcXVpZmF4MS0wKwYDVQQLEyRFcXVpZmF4IFNlY3VyZSBDZXJ0
aWZpY2F0ZSBBdXRob3JpdHkwHhcNMDIwNTIxMDQwMDAwWhcNMTgwODIxMDQwMDAw
WjBCMQswCQYDVQQGEwJVUzEWMBQGA1UEChMNR2VvVHJ1c3QgSW5jLjEbMBkGA1UE
AxMSR2VvVHJ1c3QgR2xvYmFsIENBMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIB
CgKCAQEA2swYYzD99BcjGlZ+W988bDjkcbd4kdS8odhM+KhDtgPpTSEHCIjaWC9m
OSm9BXiLnTjoBbdqfnGk5sRgprDvgOSJKA+eJdbtg/OtppHHmMlCGDUUna2YRpIu
T8rxh0PBFpVXLVDviS2Aelet8u5fa9IAjbkU+BQVNdnARqN7csiRv8lVK83Qlz6c
JmTM386DGXHKTubU1XupGc1V3sjs0l44U+VcT4wt/lAjNvxm5suOpDkZALeVAjmR
Cw7+OC7RHQWa9k0+bw8HHa8sHo9gOeL6NlMTOdReJivbPagUvTLrGAMoUgRx5asz
PeE4uwc2hGKceeoWMPRfwCvocWvk+QIDAQABo4HwMIHtMB8GA1UdIwQYMBaAFEjm
aPkr0rKV10fYIyAQTzOYkJ/UMB0GA1UdDgQWBBTAephojYn7qwVkDBF9qn1luMrM
TjAPBgNVHRMBAf8EBTADAQH/MA4GA1UdDwEB/wQEAwIBBjA6BgNVHR8EMzAxMC+g
LaArhilodHRwOi8vY3JsLmdlb3RydXN0LmNvbS9jcmxzL3NlY3VyZWNhLmNybDBO
BgNVHSAERzBFMEMGBFUdIAAwOzA5BggrBgEFBQcCARYtaHR0cHM6Ly93d3cuZ2Vv
dHJ1c3QuY29tL3Jlc291cmNlcy9yZXBvc2l0b3J5MA0GCSqGSIb3DQEBBQUAA4GB
AHbhEm5OSxYShjAGsoEIz/AIx8dxfmbuwu3UOx//8PDITtZDOLC5MH0Y0FWDomrL
NhGc6Ehmo21/uBPUR/6LWlxz/K7ZGzIZOKuXNBSqltLroxwUCEm2u+WR74M26x1W
b8ravHNjkOR/ez4iyz0H7V84dJzjA1BOoa+Y7mHyhD8S
-----END CERTIFICATE-----
If you take this text (including the 'BEGIN/END' lines) and save it in a file with the extension 'cer' Windows will automatically read this as a Certificate file:
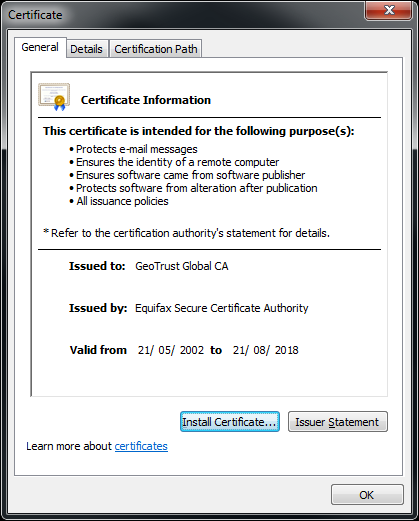
If you are running on a Linux Platform, you should have 'openssl' available by default, if you are Windows, you'll need to install it.
-or-
2. Use a browser to attach to the REST endpoint directly:
So ; this is just 'google.co.uk' viewed in Chrome - The Endpoint NOT a REST endpoint (but that doesn't matter here).
Click on the padlock:
![]()
Then 'Security | View Certificate':
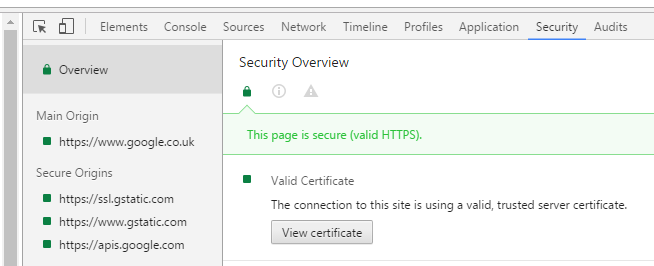
NOTE: if you get a Certificate error when you access the REST endpoint : this (probably) indicates that the REST Endpoint is not using a CA-Signed Certificate, but instead using a Self-Signed Certificate.
If the Endpoint is using a Self-Signed Certificate (or even a 'Corporate CA Signed Certificate); then your browser - and more importantly Java will not trust the Certificate; and will refuse to complete the SSL connection.
To inform Java (well in this case more specifically PRPC) to trust the endpoint's Certificate - you need to include it (or more likely the signing Certificate) in a Java Truststore (confusingly called a 'keystore' in the general sense, even though it doesn't necessarily include any key-pairs).
For Java in general: you would import the Certificate in the Java file:
JAVA_HOME\jre\lib\security\cacerts
You use the JDK 'keytool' for this: see here for an example : http://stackoverflow.com/questions/4325263/how-to-import-a-cer-certificate-into-a-java-keystore
For PRPC - you create a 'Keystore Rule' and reference it from your Connector (depending on your version of PRPC; you may need to do this at 'CACERTS' level).
Mastercard
US
Hello PRITJ,
I am a colleague of Nishant. In this scenario, we are using MSSL. It's a two-way handshake.
Also, pega is the service provider in this scenario. We are backend system and maintaining the workflow of the front end app.
Thanks
Dheeraj
Pegasystems Inc.
GB
If you are using TWO-WAY SSL: then you'll need to ensure you have provided PRPC with a Keypair (a private key and a public key/Certificate).
Have you done this ? (I'm not sure, without checking a system, how you do with this PRPC REST CONNECTORs - is there a 'slot' on the Rule Form for this ?)
Pegasystems Inc.
GB
Additionally: make sure you have configured the REST ENDPOINT using its HOSTNAME, rather than its IP address (or more accurately - make sure the 'CN' string in the Certificate matches the DNS name of the server you are connecting to).
When you say this work in a lower-environment; is that PRPC system talking to the SAME REST endpoint, or an equivalent REST endpoint ?
Mastercard
US
Lower environment is Dev and over there we are not having any certificates. Front end app is sending request to our system(PRPC) via ESB and we are sending the response back to front end app via ESB. Endpoints are different.
Pegasystems Inc.
GB
When you say that your DEV system is "not having any certificates" : do you mean that DEV is using HTTP rather than HTTPS ?
Virtusa
US
Hi
Check what version of TLS you are using. If you are using >=TLS v1.2 you might see this issue. if TLS version is higher then you might need to put in some changes in Invoke Rest Connector activity.
Thanks
Sam
Bank Of America
IN
Hello,
I really appreciate your efforts, if you can let us know the exact changes that needs to be performed and in which step.
Thanks in advance.
Ganag.
Incessant Technologies
US
Hi,
I am also facing this exception.We are using pega 7.2 and protocol sending as TLSv1.2.
Please suggest what changes i need to do ?
thanks
Pegasystems Inc.
GB
All things being equal; this error:
****javax.net.ssl.SSLPeerUnverifiedException: peer not authenticated
is most likely due to not having setup Trusted Certificates; and is an error that is occurring at a much lower level than PRPC itself (it's at the JVM SSL layer).
When you say you are also having this error, can you let us know some more details, for instance:
1. Did the endpoint used to work for you; but then one-day just stopped working ? (Did a Certificate Expire?)
2. If this has never worked: have you imported the endpoint's Certificate into your PRPC system ?
3. Are you able to attach other clients to this same endpoint without this error (if so: what client - a browser /SOAPUI etc?)
Thanks !
John
Updated: 29 Jun 2017 6:46 EDT
Luxoft
IN
Hi John,
We are facing similar issue.WAS team configured certificate in WAS server with dynamic outbound ssl configuration. When tried testing Connect -Soap, 403 forbidden error is thrown. WAS team ran SSL trace and found that pega is looking certificate under jvm lib\security\cacerts folder instead of path created in WAS server. Let us know if there is problem in certificate configuration. Pega version is 7.21. and WAS 8.5.5.
Thanks
Hari
Pegasystems Inc.
IN
Hi Hari,
We see that you have created a new post for this question: Transport error 403 in Connect Soap
Please continue the discussion over the new post.
Thank you,
