Customer masterkey ID in Keystore using Azure KMS Key Vault
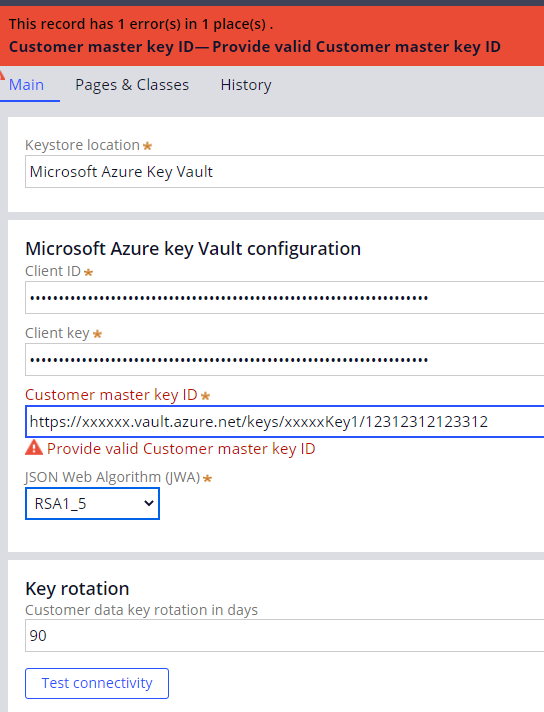
We are trying to configure a KMS key store ( and eventually refer in platform cipher in application data encryption). The Key store rule form is not able to recognize the customer master key ID of the key that we create in an Azure key vault.
we tried to give full identifier , just key ID ..either way it is throwing error saying "Provide valid Customer master key ID" ..Any inputs on what should be correct format or if we are missing anything
any suggestions/ideas are welcome. Thanks!

@MANOJPDN
To create a Microsoft Azure Key Vault keystore please follow the steps on this documentation to firstly create the keystore type:
https://docs-previous.pega.com/security/86/creating-keystore-application-data-encryption
Next, you want to configure a Microsoft Azure Key Vault keystore. The following document will walk you through that process:
https://docs-previous.pega.com/security/86/configuring-amazon-key-management-service-kms-key-rotation
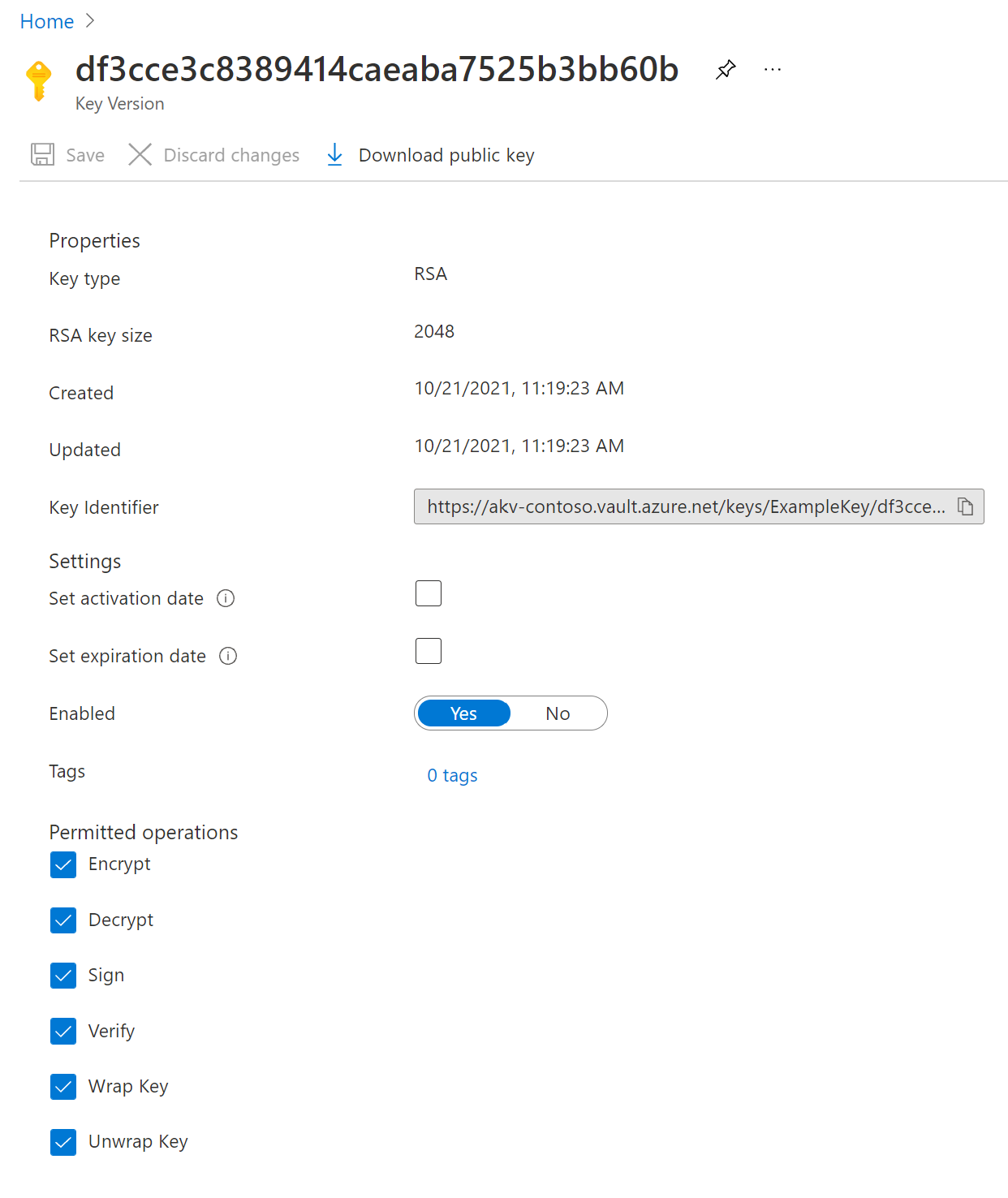
For details in creating the master key ID, please refer to the Azure key documentation
https://docs.microsoft.com/en-us/azure/key-vault/keys/quick-create-portal
Thank you