Pega continually works to implement security controls designed to protect client environments. With this focus, Pega has issued patch releases and hotfixes for three medium security vulnerabilities in Pega Platform. These issues can only be executed by users with Pega Developer access.
We would like to acknowledge Andrea Solenne, Christian Romano, and Lapo Mezzani for finding these vulnerabilities.
|
Advisory |
Description |
Impact |
Remediation |
|
C24 |
Two Cross-site Scripting (XSS) vulnerabilities:
|
Cross-site scripting (XSS) is an attack in which an attacker injects malicious executable scripts into the code of a trusted application or website. Attackers often initiate an XSS attack by sending a malicious link to a user and enticing the user to click it. In these scenarios only an authorized Pega user with developer access can perform this attack.
Clients with internet-facing applications should update or apply the hotfix. Clients running their own infrastructure should consult their security teams.
|
For both issues: 23.1.2 hotfix 23.1.3 Patch Release
24.1.1 hotfix 24.1.2 Patch Release
24.2 Patch Release |
|
HTML Injection vulnerability |
HTML Injection is an attack that is similar to cross-site scripting (XSS). While in the XSS vulnerability the attacker can inject and execute Javascript code, the HTML injection attack only allows the injection of certain HTML tags. Attackers often initiate an HTML injection attack by sending a malicious link to a user and enticing the user to click it.
|
23.1.2 hotfix 23.1.3 Patch Release
24.1.1 hotfix 24.1.2 Patch Release
24.2 Patch Release |
We are not aware of any of our clients being compromised as a result of these vulnerabilities.
The remediation for these issues will be included as part of the product in the patch releases of the Pega Platform listed above. Hotfixes for Pega Platform 23.1.2, 24.1.1 are available as described below.
We will not provide hotfixes on other prior versions of the Pega Platform, nor will we provide steps as part of a local change.
If you are a Pega Cloud® client, your Pega Cloud environments running the relevant Pega versions listed in the table below are being proactively remediated by Pega. Cloud Maintenance (CM) cases are being created for each of your environments which provides the schedule of when the hotfixes will be applied.
If you are a United States Pega Cloud for Government (PCFG) client, Cloud Service Request (SR) cases are being created which will provide the relevant hotfixes for you to apply to your PCFG environments.
If you are an on–premises or client managed cloud client, please review the table below to determine which hotfixes correspond to your Pegasystems installation.
Once you have determined the appropriate hotfix IDs, you can now download your hotfix directly from My Security Hotfixes on My Pega.
This facility enables self-service access to security hotfixes, without the need to raise a support ticket.
As always, be sure you have appropriate backups in place before applying the hotfixes.
As always, we recommend our clients review our Security Checklist regularly.
Hotfixes
Hotfixes are being created only for the latest Pega Platform patch releases in standard support (23.1.2 and 24.1.1). We will not provide hotfixes on prior versions of Pega Platform.
As a best practice, you should update your Pega environment to the latest release to take advantage of the latest features, capabilities, security and bug fixes. For more detailed information see Keeping current with Pega.
|
Pega Platform Version |
XSS issue with App name |
XSS issue with case type |
HTML Injection issue with Stage |
|
23.1.2 |
HFIX-B1811 |
HFIX-B1768 |
HFIX-B1770 |
|
24.1.1 |
HFIX-B1812 |
HFIX-B1767 |
HFIX-B1769 |
|
24.2 |
Fixed in release |
Fixed in release |
Fixed in release |
Dates for upcoming patch releases can be found here: Pega Infinity Patch Calendar.
For HFIX-B1811 and HFIX-B1812, the following additional manual steps are needed:
- Open the function rule as shown below:
GridHeaderElements--(StringBuffe2ceb5a8fa884b8fb8c9cc7705d04e287
(For HFIX-B1811 ruleset version is 08-23-04 and for HFIX-B1812 ruleset version is 08-24-03)
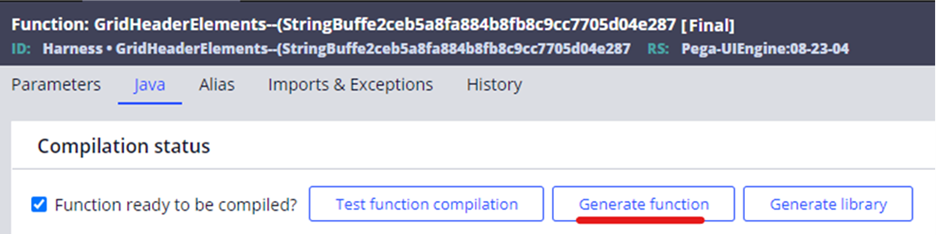
- Select the Java tab
- Click Generate function. A pop-up page will show a successfully generated message.
- Locate the following DSS (pyPreventXSSInLabel) on your system and change the value from false to true.
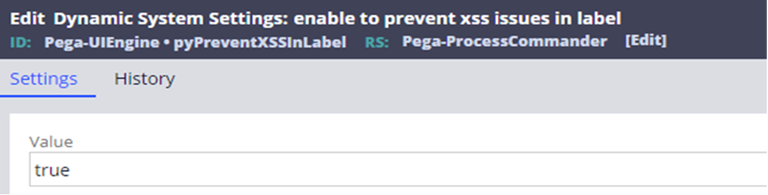
The setting is described further in this article: Preventing risk of XSS attack when specifying label controls
- A restart is needed for the changes to take effect.
CVE Details
|
CVE Details |
XSS issue with App name |
XSS issue with case type
|
HTML Injection issue with Stage
|
|
Software/Product |
Pega Platform |
Pega Platform |
Pega Platform |
|
Affected Version(s) |
From 8.1 to 24.1.2 |
From 8.1 to 24.1.2 |
From 8.1 to 24.1.2 |
|
CVE ID |
CVE-2024-6700 |
CVE-2024-6701 |
CVE-2024-6702 |
|
CVSS Rating |
Medium – 5.5 |
Medium – 5.5 |
Medium – 5.2 |
|
Description |
Cross Site Script (XSS) vulnerability |
Cross Site Script (XSS) vulnerability |
HTML Injection vulnerability |
If you have any questions or concerns, please raise a Support ticket with Global Client Support in My Support Portal for assistance.
