Improper Access Control - Constellation AppStatic service
Pega continually works to implement security controls designed to protect client environments. With this focus, Pega has issued hotfixes and patch releases for one critical security vulnerability in Pega Platform.
|
Advisory |
Description |
Impact |
Remediation |
|
B25 |
Improper Access Control
|
Insufficient detail in JWT token that describes the permissions for the user may allow unintended access to the Constellation AppStatic Service data.
This affects those clients that are using Constellation AppStatic Service. All clients are recommended to install the hotfix and to deploy the Constellation App Static service version 1.31 or higher to ensure your system is protected.
|
8.8.5 Hotfix 23.1.0 to 23.1.4 Hotfix 24.1.0 to 24.1.2 Hotfix 24.2.0 Hotfix 23.1.5 Patch Release 24.2.1 Patch Release 25.1.0 Release
- AND-
|
We are not aware of any of our clients being compromised as a result of this vulnerability.
The remediation for these issues will be included as part of the product in hotfixes and patch releases of the Pega Platform listed above.
We will not provide hotfixes on prior versions of the platform other than those listed for this Security Advisory. We will not provide steps as part of a local change.
If you are a Pega Cloud® client, your Pega Cloud® environments running the relevant Pega versions listed in the table below, are being proactively remediated by Pega. Cloud Maintenance (CM) cases are being created for each of your environments and will provide the schedule of when the hotfixes will be applied. If you are not on a version with a solution provided, you need to upgrade as soon as possible.
If you are a United States Pega Cloud for Government (PCFG) client, Cloud Change (CC) cases are being created for the relevant hotfix, which will be applied by Pega. If you are not on a version with a solution provided, you need to upgrade as soon as possible.
If you are an on–premises or client managed cloud client, please review the tables below to determine which hotfixes correspond to your Pegasystems installation. Once you have determined the appropriate hotfix IDs, you can download your hotfix directly from My Security Hotfixes on My Pega.
Information regarding the availability of the hotfixes will be publicly posted on Pega Support Center on April 23, 2025 (90 days) in order to give all Pega clients time to patch their systems, we request that clients not discuss this in public forums until after it’s been publicly posted.
As always, we recommend our clients review our Security Checklist regularly.
Hotfixes
Remediation will include hotfixes and patch releases for versions listed in this Security Advisory. In addition to the hotfix, clients must deploy the Constellation App Static service version 1.31 or higher. A restart is needed after the hotfix is installed.
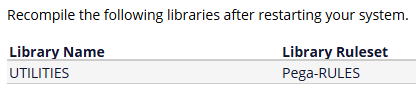
After restarting, open the following library and click the Generate Library found on the page:
![]()
As a best practice, you should update your Pega environment to the latest release to take advantage of the latest features, capabilities, and security and bug fixes. See Keeping current with Pega.
|
Version |
Hotfix |
|
8.7.6 |
*N/A |
|
8.8.5 |
HFIX-C383 |
|
23.1.0 |
HFIX-C336 |
|
23.1.1 |
HFIX-C315 |
|
23.1.2 |
HFIX-C335 |
|
23.1.3 |
HFIX-C334 |
|
23.1.4 |
HFIX-C333 |
|
24.1.0 |
HFIX-C340 |
|
24.1.1 |
HFIX-C338 |
|
24.1.2 |
HFIX-C337 |
|
24.2.0 |
HFIX-C339 |
*Please contact Pega Support if you are using Constellation on version 8.7.6
Dates for upcoming patch releases can be found here: Pega Infinity Patch Calendar.
Issue Details
|
Issue Details |
Insufficient detail in JWT token |
|
Software/Product |
Pega Platform |
|
Affected Version(s) |
From 8.7 to 24.2.0 |
|
CVE ID |
No CVE |
|
CVSS Rating |
Critical – 9.1 |
|
Description |
Improper Access Control |
If you have any questions or concerns, please raise a Support ticket with Global Client Support in My Support Portal for assistance.
