Question
Pegasystems Inc.
IN
Last activity: 3 Nov 2022 7:27 EDT
URL Tampering vulnerability detected.
We are observing a "URL tampering vulnerability detected" error sporadically in our environment post the upgrade to Pega 8.4. (Attached is the screenshot) The users who are observing it are set up correctly as per their access group and as far as I see, we are not accessing or referring to the activity which is listed in the error details.
Does anyone have any specific thoughts on what is causing this issue or how we can fix it? I found this reference - https://community.pega.com/knowledgebase/articles/security/verifying-requests-application-layer but I do not want to turn off the display of warnings without understanding the root cause.
***Edited by Moderator Marissa to update Platform Capability tags****
***Edited by Moderator: Pallavi to update Support Case Details***
-
Likes (5)
Srikanth Veeraneni Manjunatha Prasad HR Manish Kumar Nagarjuna Ramanaboina Dmitriy Barykin -
Share this page Facebook Twitter LinkedIn Email Copying... Copied!
Pegasystems Inc.
IN
Hi,
Please provide the details by click "view details" from error.
Virtusa
SG
On click of View Details, it will open the Logs Screen.
Pegasystems Inc.
IN
The details are already captured in the screenshot I provided with the issue.
Pegasystems Inc.
IN
You will also see a browser console log with the call stack. Refer screenshot:
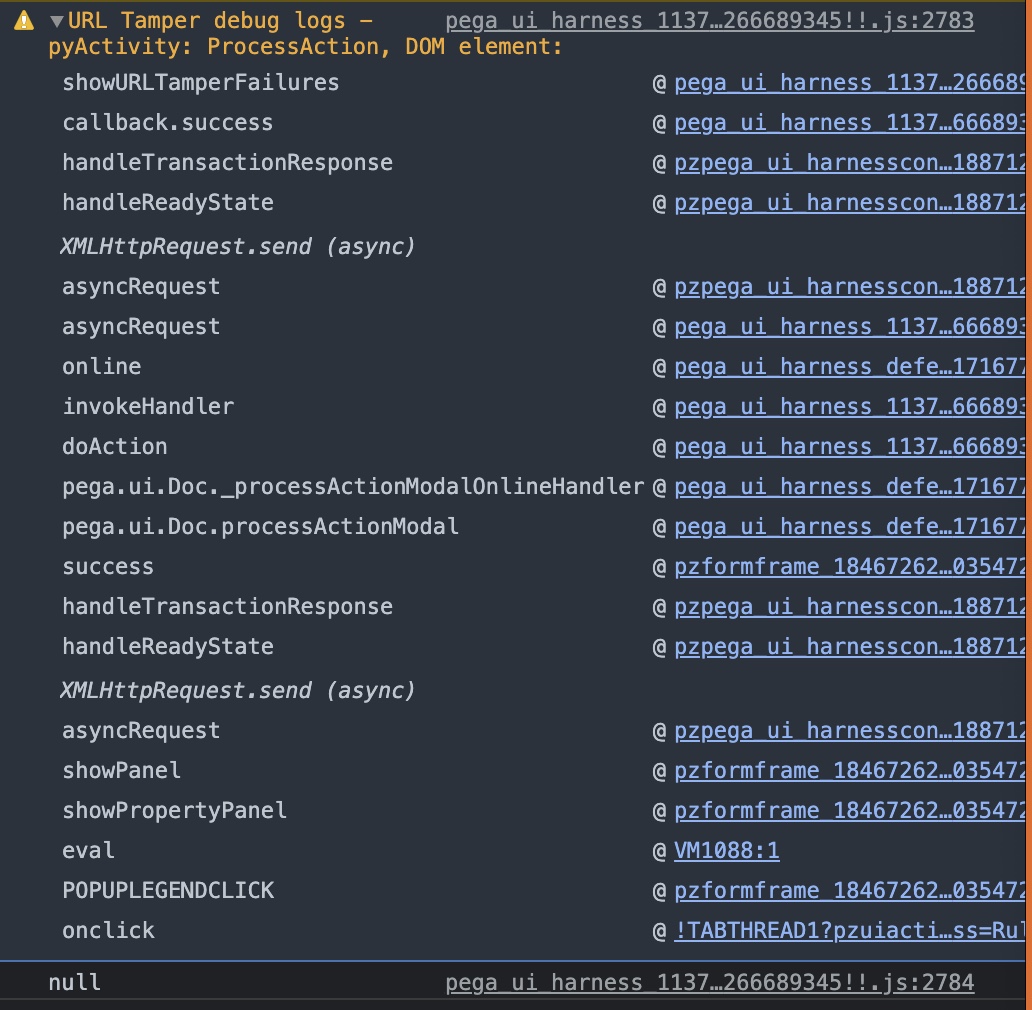
Pegasystems Inc.
IN
It most probably is a platform bug. You may need to open a Product Support ticket to get a proper fix.
Pegasystems Inc.
US
@machs1
If you open a Support Case, please let us know the ID for it so that we may track it for you!
Thanks!
Marissa | Senior Moderator | Pega Collaboration Center
SiXworks
GB
We are seeing this too since upgrading to 8.4.1
Pegasystems Inc.
US
Hi Machs1,
Please open an SR with Pega Support to have this looked at. You can reply with the SR number here.
Thanks!
Pegasystems Inc.
US
Hi Andrew,
Please open an SR with Pega Support to have this looked at. You can reply with the SR number here as well
Thanks!.
-
Andrew Webster
SiXworks
GB
INC-130774 raised
Pegasystems Inc.
AU
Hi, We are having the same issue on 8.4.0 - please let me know if this a platform bug
SiXworks
GB
@dsoud - Probably. My SR is progressing and we are on 8.4.1, so any fix is likely to be 8.4.2 or 8.4.3
Pegasystems Inc.
IN
This is an experimental feature for 8.4 , and is by default turned off. The feature is fully available and shipped in 8.5. In 8.4 the warnings are turned off for production environments and show up only in lower level environments as a preview.
However these lower environments warnings too would be turned off in next patch release.
-
Maciek Surdziel Guangri Liang Phil Shannon
Stratosphere Technical Consulting
US
Hi Suman,
What exactly are you referring to when you say that it "is by default turned off"?
Based on the descriptions outlined in https://community.pega.com/knowledgebase/articles/security/verifying-requests-application-layer , the only thing that is completely off by default is pyBlockUnregisteredRequests.
Does this mean that in 8.5 unregistered requests will be blocked by default? We recently upgraded to 8.4.2 and are seeing this warning when running OOTB scripts on some controls and want to determine what if any changes we should expect to have to make when we upgrade to 8.5.
Pegasystems Inc.
IN
Hello Chris,
> What exactly are you referring to when you say that it "is by default turned off"?
The feature of actually blocking unregistered requests is turned off in 8.4 .
>Does this mean that in 8.5 unregistered requests will be blocked by default?
Yes.
For your custom controls you need to get familiar with these concepts. However actual application fixes /changes can be done once you upgrade to 8.5.
Stratosphere Technical Consulting
US
Hi Suman, we are in the midst of upgrading to 8.7.1 from 8.4.2 and it seems like we may not be able to use this feature reliably, and may have to simply disable pyBlockUnregisteredRequests. This is because lots of OOTB behavior seems to get rejected.
For example we have a list of assignments available on the review harness of a work object, which were being opened with the "pega.desktop.openAssignment" script in order to avoid the pop up asking if the user wanted to open a work object tab that was already open, which is what happens when using the standard Open Assignment action.
It looks like the URL generated by this script is not encrypted or registered, and our attempts to use the "Register OOTB actions used in script for URL tamper proofing" checkbox have not proven successful (it seems to fail on doUIAction, which is seemingly not run via URL if pyBlockUnregisteredRequests is turned off).
Even using the Open Assignment action, which would throw an undesired dialog on the screen about opening a tab again, we get 403 errors when the user confirms that they do want to open the tab again.
Is there any kind of work around for OOTB actions/scripts like this, or are there plans to encrypt/register them in some future release? As is, it seems like we have little choice but to turn pyBlockUnregisteredRequests off.
Updated: 14 Dec 2020 4:00 EST
Lanit
RU
Hello Suman,
What do you mean by unregistered requests? We don't have custom controls in our application, yet when browser is refreshed we see "URL tampering vulnerability detected". We use Data Page with REST Connector to get data from service when loading UI, all associated rules are accessible under user's Access Group.
update: Message "URL tampering vulnerability detected" appears in Dev Studio too, when you search for rule. Pega 8.4.3
KPMG
ES
Hi all, I am facing the same issue, did you find any way to solve it?
Updated: 23 Oct 2020 5:12 EDT
Glidewell dental
IN
I'm also facing same issue ,did you find the solution ?
Infosys Ltd
IN
The pyShowSecureFeatureWarnings When rule evaluated to true. As a result, the warning message dynamic layout was displayed.
Perform the following local-change:
Modify the pyShowSecureFeatureWarnings When rule to evaluate to false.
-
Jeremy Becker
Genworth Financial
US
@ArijitS7084 Brilliant. Thank you. This was driving me nuts for days.
