Question
Common Wealth Bank of Australia
AU
Last activity: 24 May 2019 6:24 EDT
Pega Federated SP server for SAML SSO
Landscape
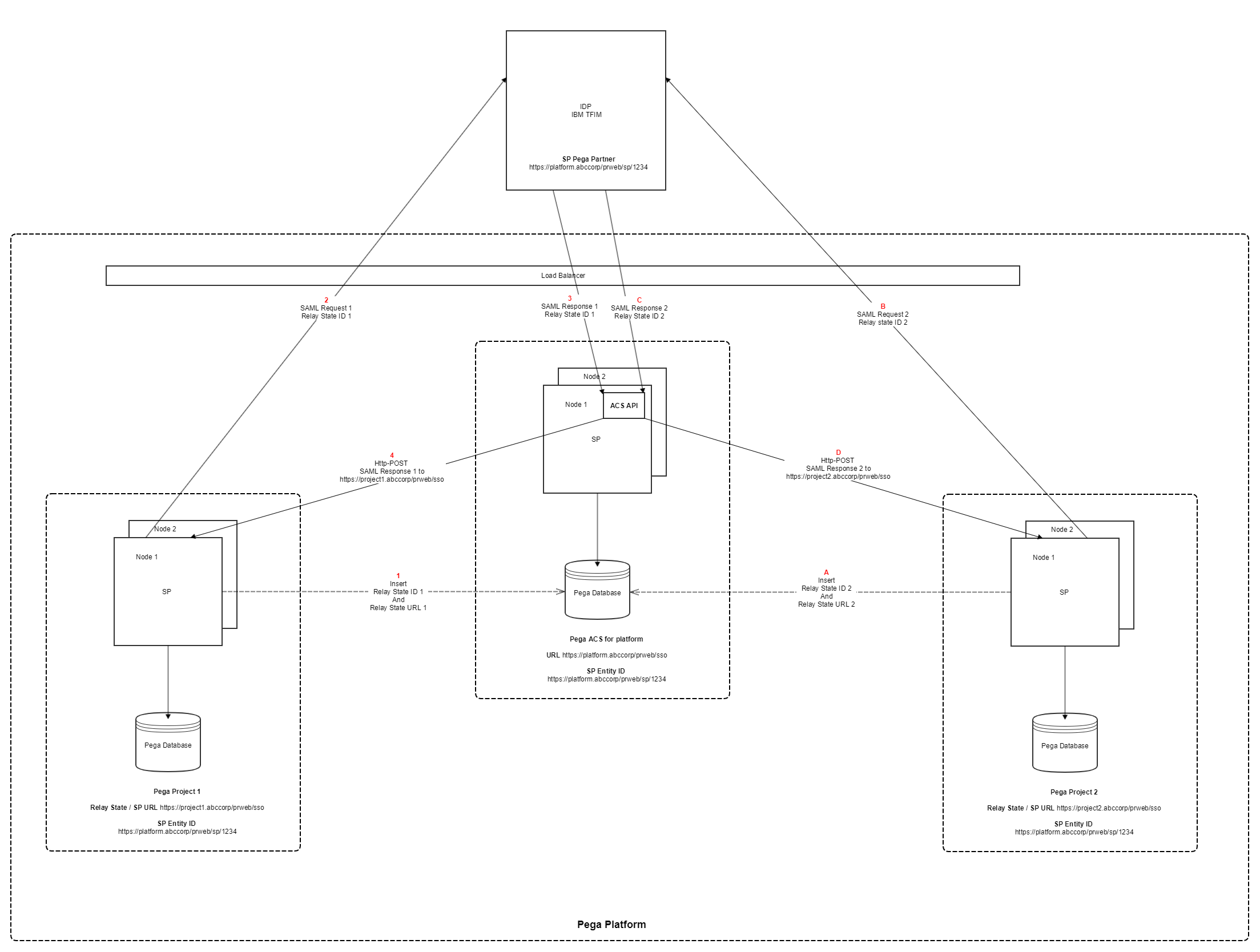
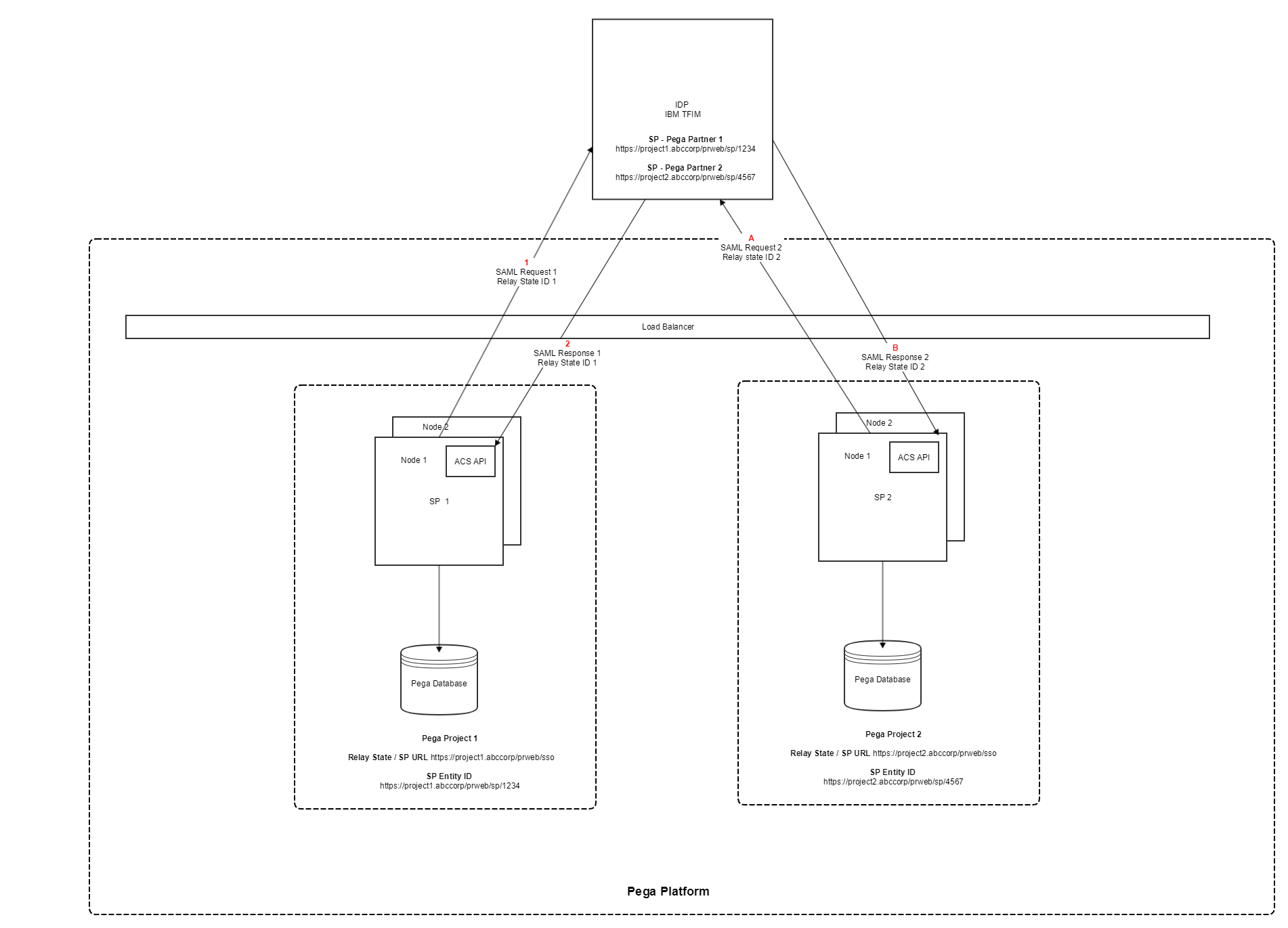
We are running a Pega platform which is hosting pega instances for multiple projects. The load balancer is common for the platform but the pega instances are separate for each of the project (i.e. Each of the project will have its own Pega Database)
Problem Statement
SSO setup has to be done separately for each of the projects on the platform though the IDP and the set of attributes returned as part of the SAML response are same. So, we are planning to do a single integration between the IDP and the Pega Platform
Design Approach
Setup a dedicated Pega instance for the platform which will potentially host the ACS endpoints acting as router of the SAML Response
These ACS endpoints will receive the SAML Response from the IDP & route them to the respective tenant of the Pega platform
The tenant will then validate the SAML token and finally authenticates the user
Though the above solution theoretically works but becomes a single point of failure (considering the huge customer base that the ACS has to handle as part of the login flow in a dozen of pega applications)
Also this violates the Pega's OOTB SSO design of having the ACS in the same instance of the SP
Any thoughts on this solution would be highly appreciated.