Question
Parana Banco
BR
Last activity: 8 Nov 2024 8:16 EST
How to manipulate operator ID during OIDC authentication
I have an SSO Open ID Connect authentication configured. We are running Pega 8.8.5 in Pega Cloud.
I have a requirement due to the pattern of IDs created on the IDP side: they have an hyphen as part of the user identifier.
Pega doesn't allow hyphen character in Operator ID when you try to create it manually.
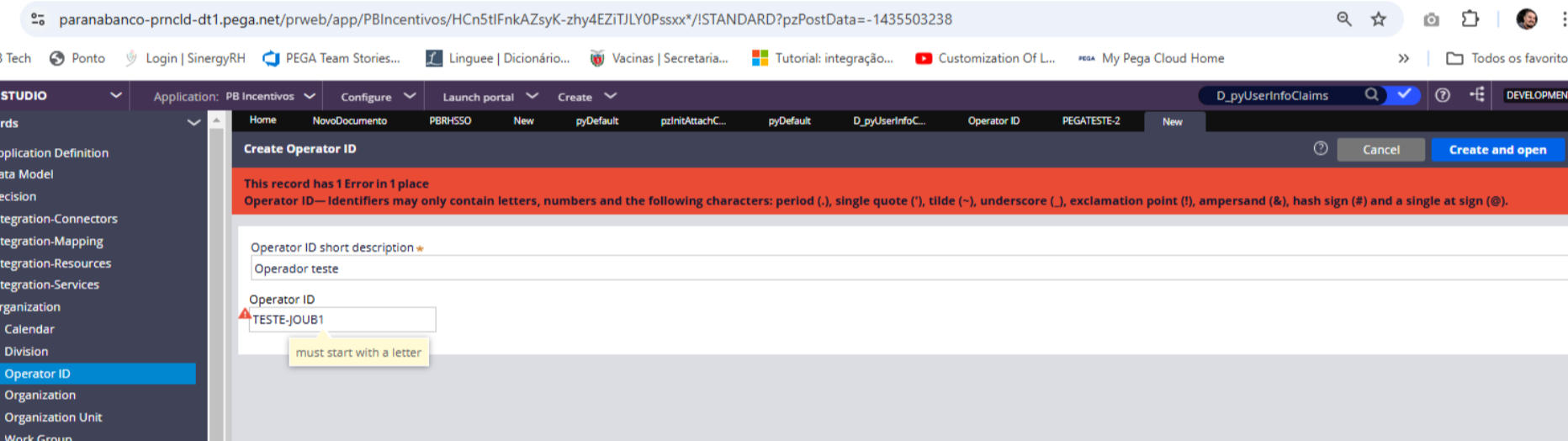
In my OIDC, I've configured the operator provisioning based on Model Operator, and the new operator is created on the fly on first login, and in that case Pega does allow the hyphen as part of user identifier.
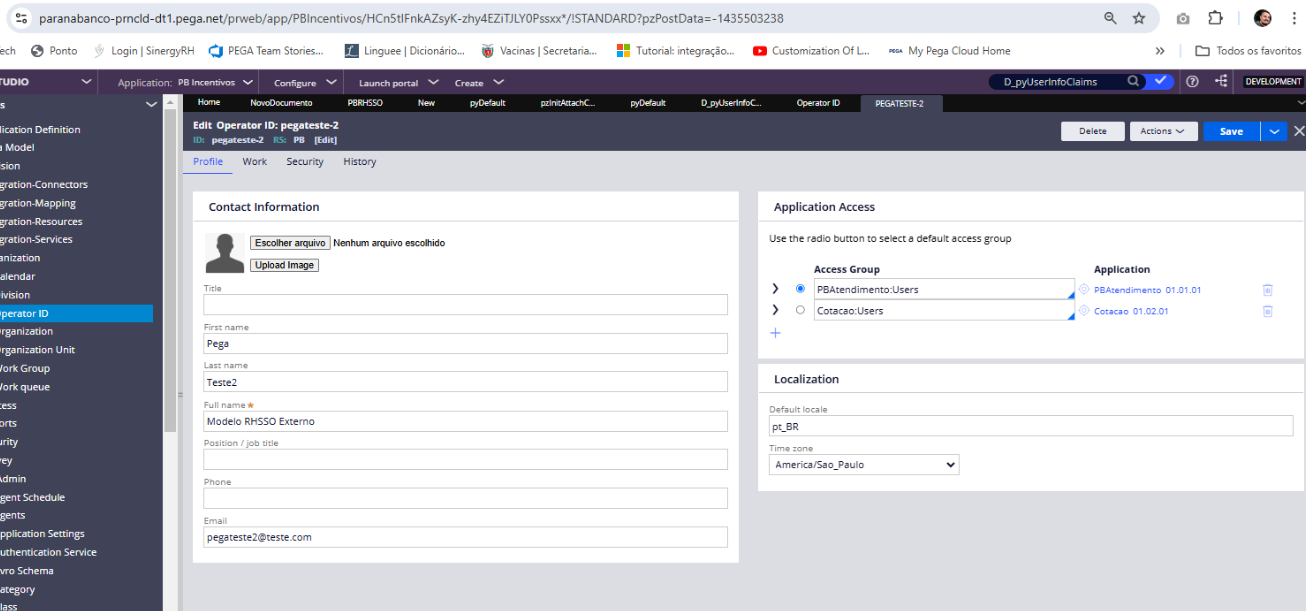
My issue is: we are switching from LDAP to SSO OIDC authentication. In LDAP, I was able to customize the
AuthenticationLDAPVerifyCredentials activity and manipulate the pyUserIdentifier during operator creation based on Model Operator, being able to replace the hyphen by an at @ sign after user got authenticated in LDAP.
I have an SSO Open ID Connect authentication configured. We are running Pega 8.8.5 in Pega Cloud.
I have a requirement due to the pattern of IDs created on the IDP side: they have an hyphen as part of the user identifier.
Pega doesn't allow hyphen character in Operator ID when you try to create it manually.

In my OIDC, I've configured the operator provisioning based on Model Operator, and the new operator is created on the fly on first login, and in that case Pega does allow the hyphen as part of user identifier.

My issue is: we are switching from LDAP to SSO OIDC authentication. In LDAP, I was able to customize the
AuthenticationLDAPVerifyCredentials activity and manipulate the pyUserIdentifier during operator creation based on Model Operator, being able to replace the hyphen by an at @ sign after user got authenticated in LDAP.
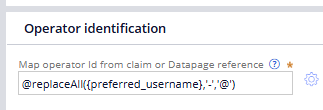
Since all my current production users are already created replacing the "-" by "@" on Operator ID, I'm trying to replicate the same behavier on Authentication Service with OIDC and so far I wasn't able to achieve that.
I've tried using expression to replace the characters directly in the "Map id from claims":
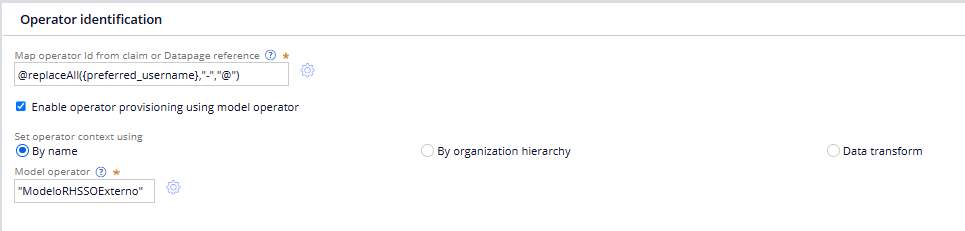
That didn't work. Tried using Data Transform instead of Model Operator, and in the DT try to set the pyUserIdentifier with the @ sign, that didn't work either.
Also tried pre and post authentication activities and so far I couldn't make it work.
My understanding is that during post authentication activity the operator would already have been created on the fly, what I need is to tell Pega to replace the hyphen by @ during operator creation.
I'm wondering if what I'm missing is a way to get the user id value from OIDC claims and pass it as input parameter to pre-authentication activity, where I can check if the operator already exisits, and if it is a new Operator then I update the pyUserIdentifier with the characters replacement.
However I don't know how to get the id value from OIDC user identifier claim during unauthenticated context of execution, or even what are the order of the events, I suppose:
1. Pre-authentication activity
2. Authenticate user against OIDC IDP
3. Operator provisioning (in my case from Model Operator)
4. Post-authentication activity
I suppose this has to happen in pre-authentication, otherwise the operator ID will be provisioned without my characters replacement. Not sure if my understanding is correct either.
I've done a lot of research, and the only post that could give me a clue for what I need in my scenario, was this one.
So I've attempted to create a similar activity containing the Java step as below:
Object dp = tools.findPage("D_pzSSOAttributes").getProperty("pyAttrList").getObjectValue();
com.fasterxml.jackson.databind.ObjectMapper om = new com.fasterxml.jackson.databind.ObjectMapper();
try{
Map<String,Object> props = om.convertValue(dp, Map.class);
Map<String,Object> preferred_username = (Map<String, Object>) props.get("preferred_username");
} catch (Exception e) {
e.printStackTrace();
}
tools.getRequestor().getRequestorPage().putString("pyAuthenticationPolicyResult", "true");With above code I suppose I should be holding the user identifier from the OIDC claims into a local variable called preferred_username. However I'm not sure how Java steps and local variable relate inside an activity.
After the above Java code, I added one step to try to open the Operator, beucause I only want to update the User ID for new operators that are going to be provisioned.
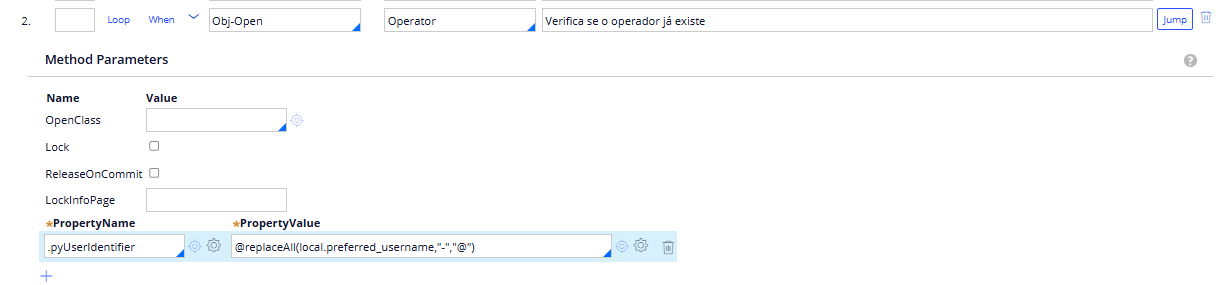
Since my Prod operator would already contain the id formar ABC@DEF, I'm checking against the replaced string from the local variable holding the user id from claims.
After that, in case it is a new Operator, I do the property-set for pyUserIdentifier.
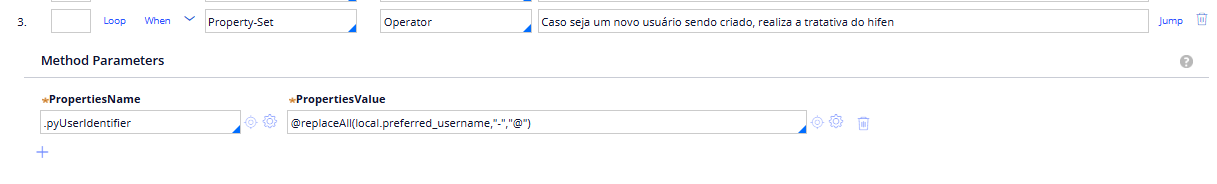
And finally, I do Save and Commit the changes on the database, and cleanup the Operator page for housekeeping.
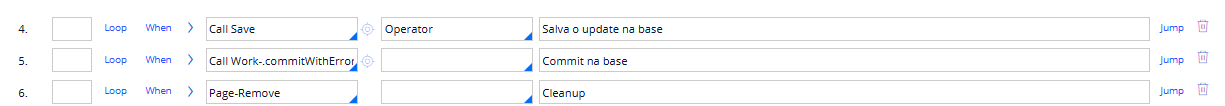
However the above described approach is not doing the job, neither in Pre or Post authentication activities.
How can I achieve that? Really appreciate any help.