Benefits of single sign-on
Single sign-on (SSO) saves time and enhances security. A client can implement SSO through SAML 2.0 to automatically sign in the application users that are created within the Pega Workforce Intelligence portal. When launching Pega Workforce Intelligence™, these users are automatically signed into the Workforce Intelligence portal. The user authentication occurs in the background before Workforce Intelligence opens. Clients have different SSO providers, including OKTA, Microsoft ADFS, and Microsoft Azure SSO, to name a few. This article provides configuration information for the different SAML 2.0 identity providers our clients have used to enable SSO for their Workforce Intelligence portal.
Before you begin
Enabling SSO is a collaborative effort between the client team and Pega team. To create the relying party inside their identity provider application, the client needs certain settings like the assertion URL and entity ID. To request the assertion URL and entity ID, follow the steps mentioned in Enabling single sign-on for the Workforce Intelligence portal.
Information for different identity providers
After obtaining the assertion URL and entity ID, the client needs to set up a replying party trust inside their identity provider. Different identity providers have different setups. The following images show the different configurations for multiple identity providers that our clients have used to enable SSO for their Workforce Intelligence portal:
- OKTA
- Microsoft Azure SSO
- Microsoft ADFS
OKTA
The following images show different configuration settings to implement SSO using OKTA. For official documentation, refer to OKTA's Build a Single Sign-On (SSO) integration.
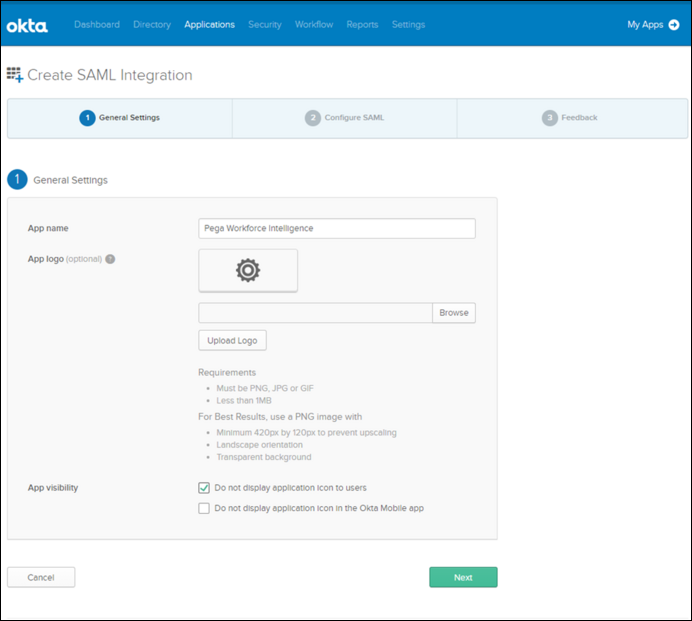
OKTA - Create SAML Integration
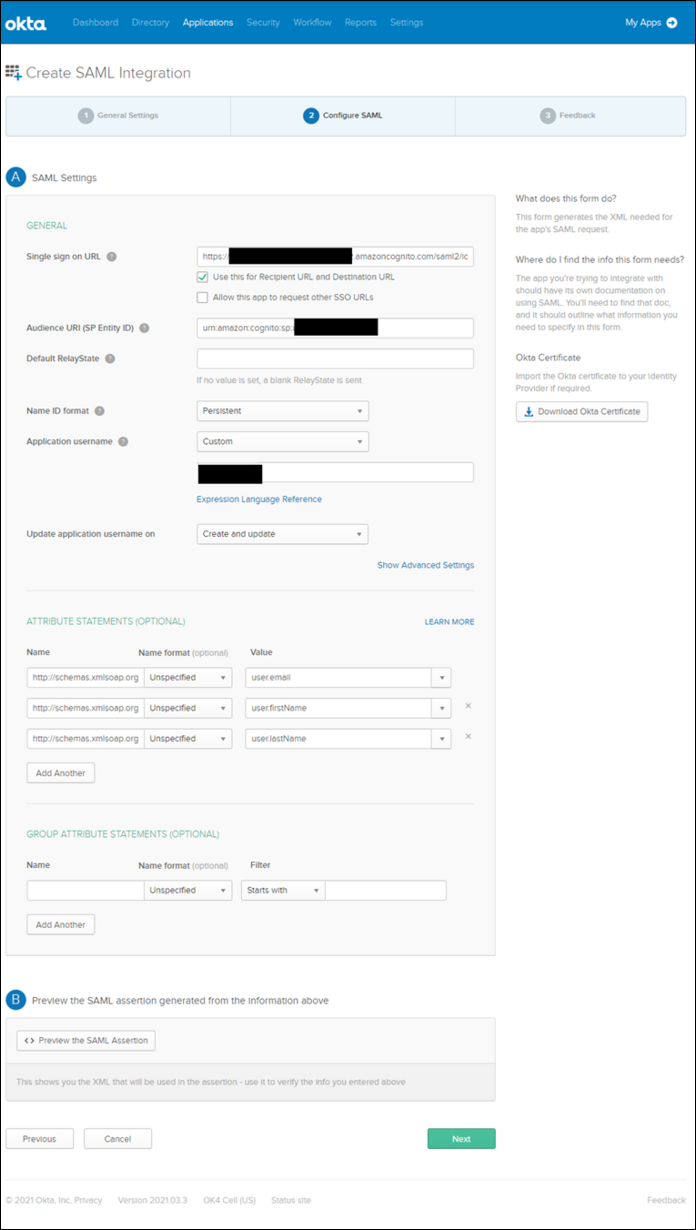
OKTA - SAML Settings
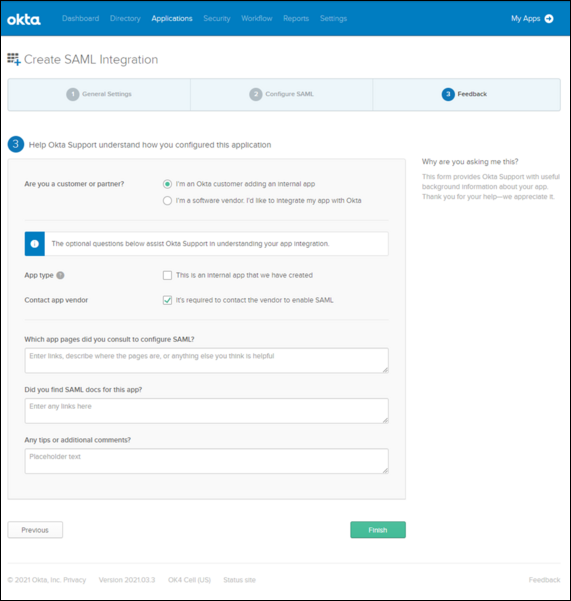
OKTA - Create SAML Integration
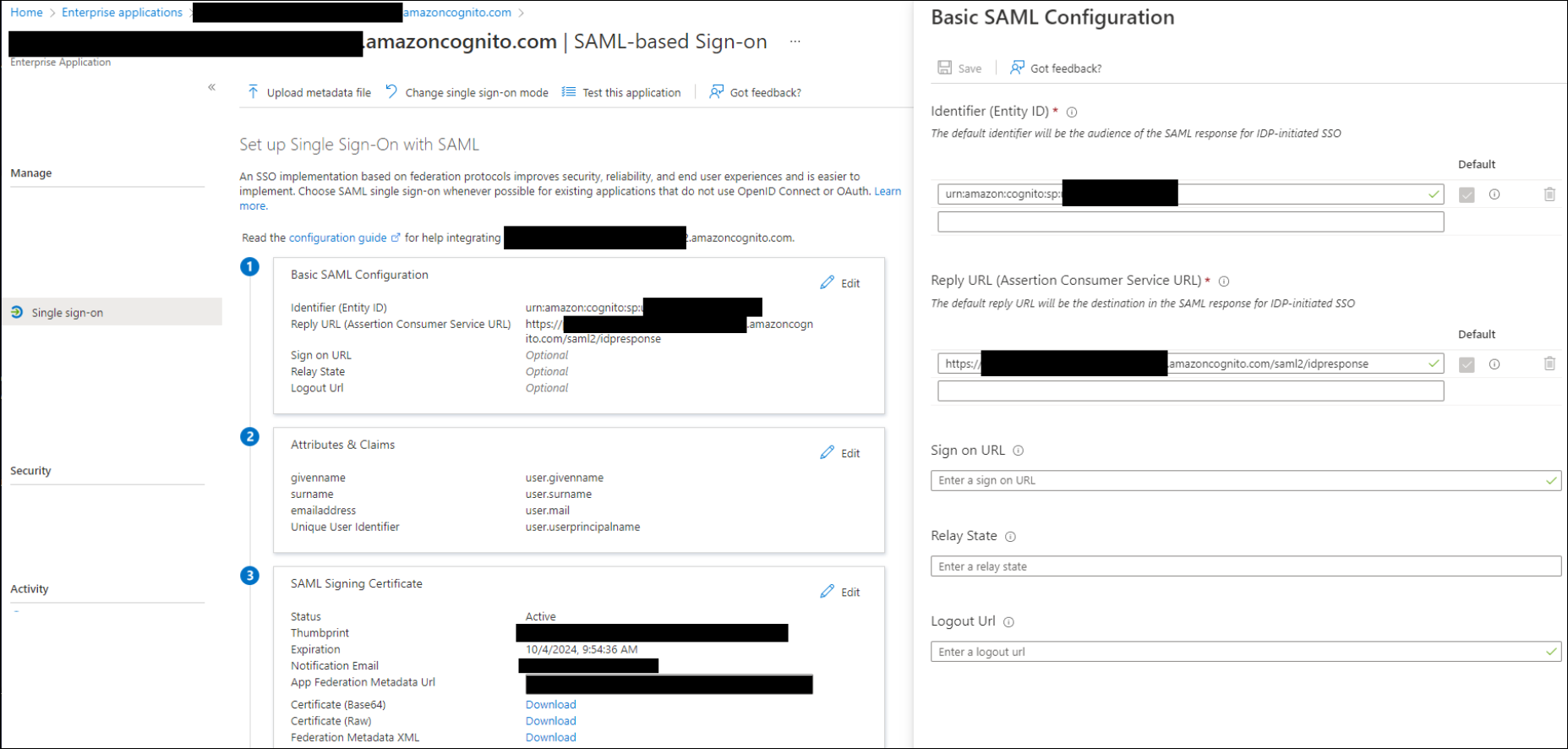
Microsoft Azure SSO
The following images show different configuration settings to implement SSO using Microsoft Azure SSO. For official documentation, refer to Microsoft's Quickstart: Enable single sign-on for an enterprise application.
Microsoft ADFS
The following images show different configuration settings to implement SSO using Microsoft AD FS. For official documentation, refer to Microsoft's Create a Relying Party Trust.
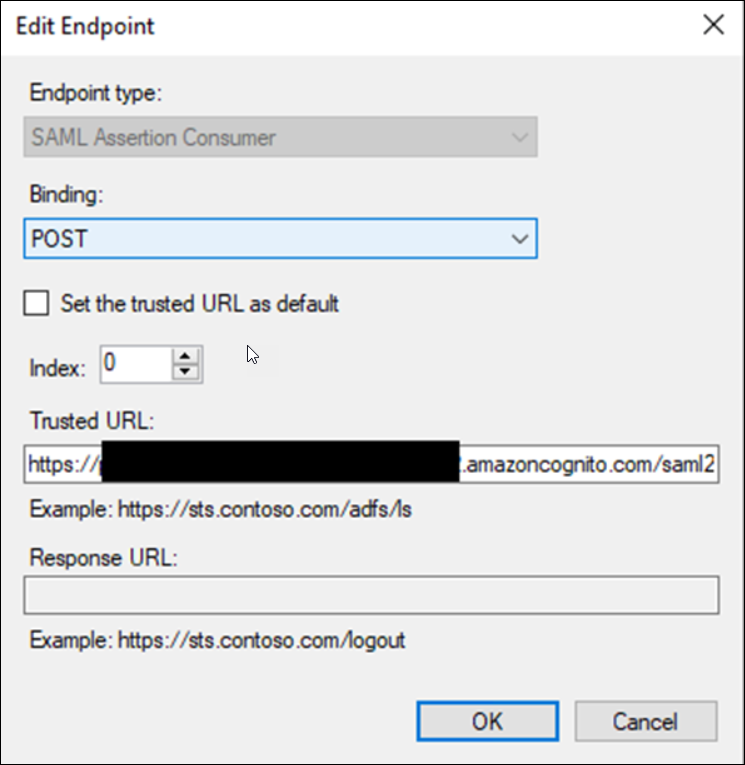
ADFS - Edit Endpoint & add Assertion URL
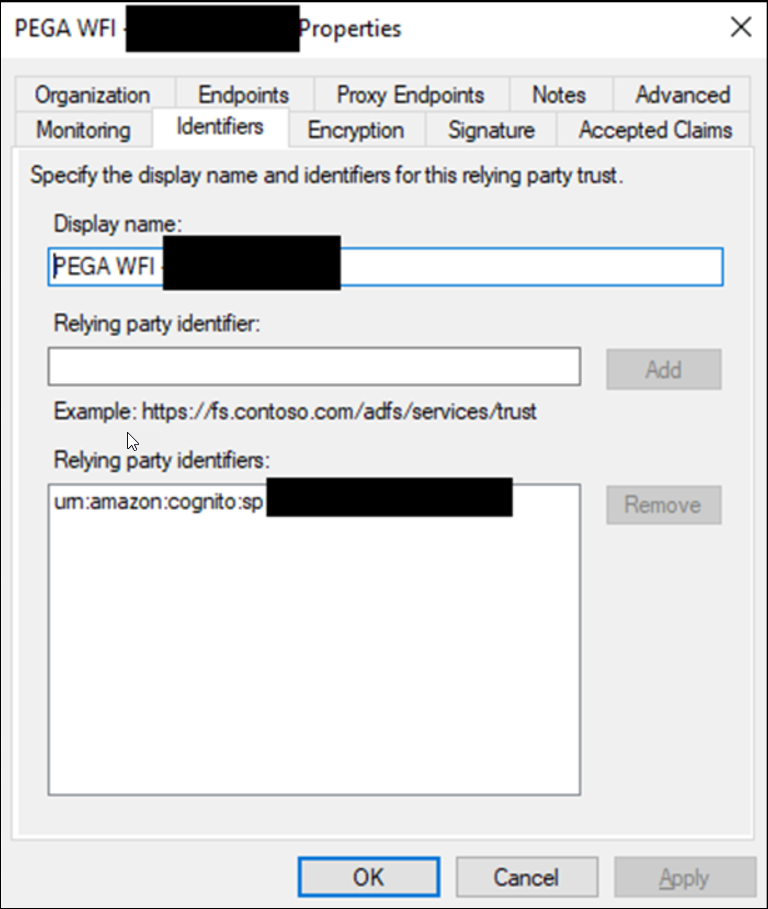
ADFS - Entity ID Tab
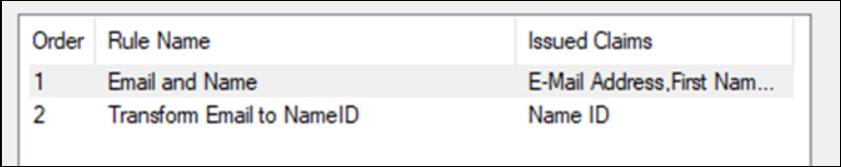
ADFS - Claim Rules
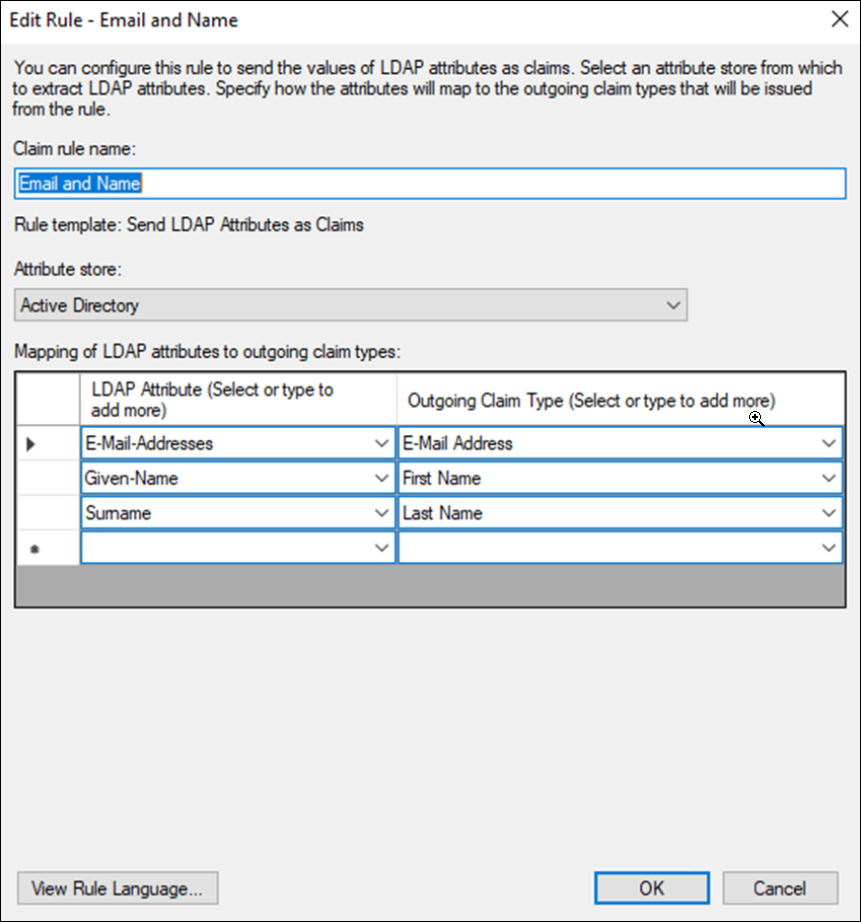
ADFS - Claim Rules Info
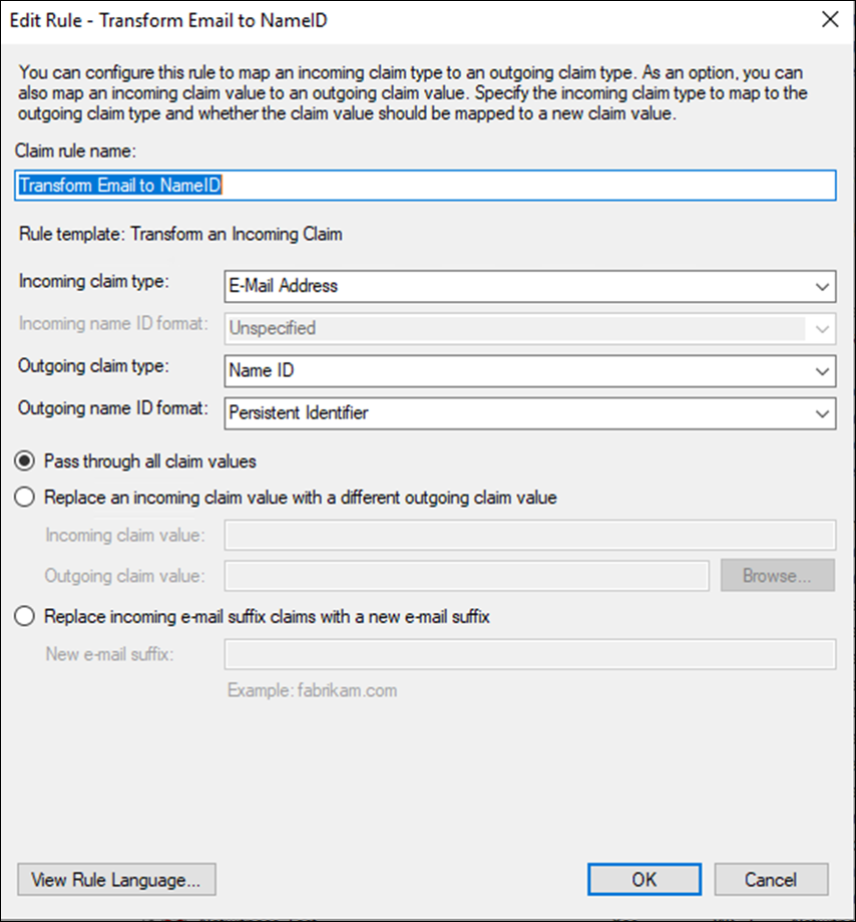
ADFS - Claims Transform
Additional Information
- For more information on SSO implementation, refer to Implementing Single Sign On.
- Initiate the SSO enablement by opening a support ticket. Refer to Enabling single sign-on for the Workforce Intelligence portal.
