Issue
After the release of Chrome version 139.X.X (built on Chromium), users experience failures when launching the LiveUI inspector in Pega applications when using a content security policy (CSP) in the application.
Symptoms and Impact
After opening Live UI, the tree panel does not display any values and constantly displays status "Loading..." .
When launching Live UI with the tree panel expanded, the Console displays a log error:
“Refused to create a worker from 'blob:https://example.com/baff24461dfc' because it violates the following Content Security Policy directive: "child-src 'self'". Note that 'worker-src' was not explicitly set, so 'child-src' is used as a fallback.”
Developers are unable to use Live UI for troubleshooting, which is critical for diagnosing and resolving platform issues.
Steps to reproduce
-
Log into Dev Studio
-
Go to -> -> .
-
Locate and select the configured CSP Policy name used by your application.
-
Edit Content Security Policy to Disable Data and Blob for Child Frame-Source.
-
Refresh the browser tab and open Live UI.
Root Cause
This is a known issue caused by the changes Google made in the latest Chromium 139 update which affects browsers like Chrome and Edge. Live UI generates blob-based workers (e.g. new Worker(blobURL)). When the worker-src directive is not explicitly defined, Chrome falls back to the child-src directive.
If child-src is set to Self, it excludes blob: URLs, which are required for Live UI worker script creation. Google introduced a security change that causes the browser to fire an error event when a Content Security Policy (CSP) blocks a Worker script. This results in the browser blocking the functionality.
Solution
For applications using custom CSP
Use a workaround to add “blob: “ URL’s to the list of Allowed websites in the CSP. Add these to the child-src directive in the CSP rule mapped to the application along with Self option.
-
Log into Dev Studio
-
Go to -> -> .
-
Locate and select the configured CSP policy name used by your application.
There are two types of configurations the user can make at this point:
Configuration 1:
This is our recommended configuration as it is the most secure:
-
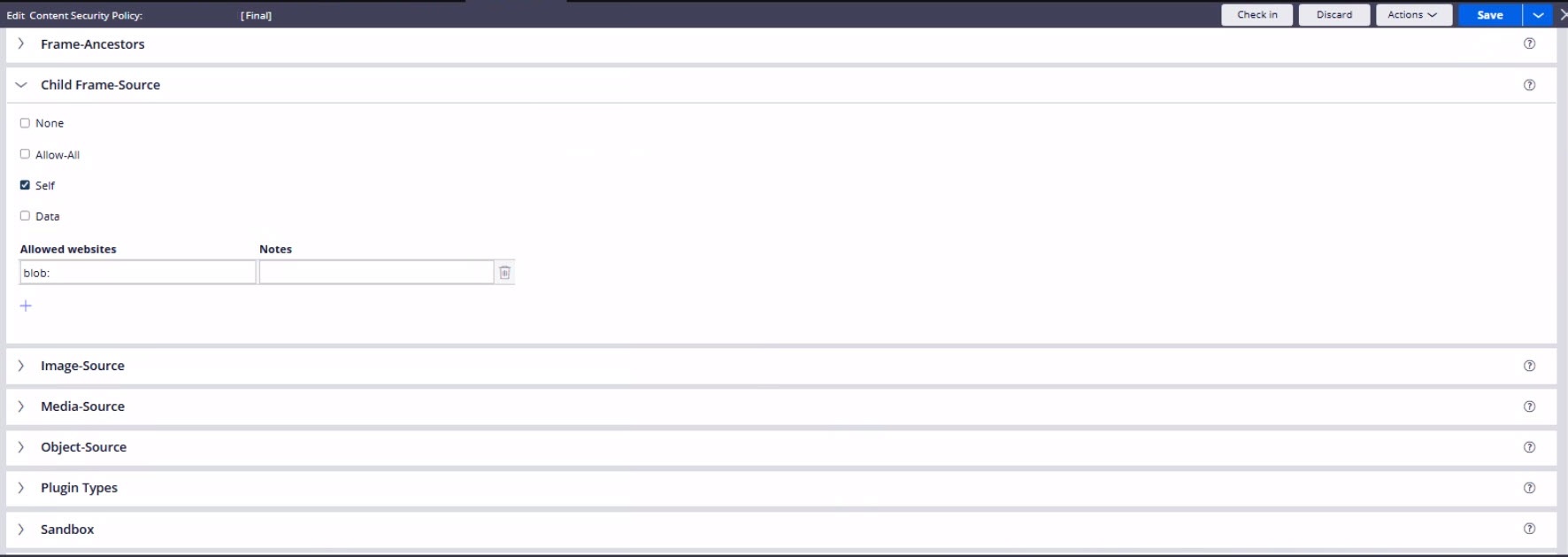
In the Child Frame-Source section, add "blob:" to the list of allowed sources.
The updated directive should include both Self and 'blob:' to maintain security while enabling Live UI.
Configuration 2:
This is for scenarios where your business requires that you use the option Allow-All instead of Self for the child-src directive:
- Select the option Data in the Child Frame-Source section. Enabling the Data checkbox implicitly enables the "blob:" directive.
For applications using OOTB CSP
The OOTB Content Security Policy rule pxDefaultSecured has been fixed in the following releases:
-
Pega Infinity™ '24.2.3
-
Pega Infinity '25.1.1
This documentation will be updated as soon as the fix for this and other OOTB CSP (pxDefaultSecured, pxDefaultAllowAll and MKTDefaultSecured) is included in other patches.
References
Chrome 139 Release Notes – Fire error event for CSP-blocked Worker
