Question
Pegasystems Inc.
AU
Last activity: 2 Feb 2016 21:09 EST
Would Pega use jdk cacert store to validate SOAP Connector - Trusted cert if it cannot find the client cert in assigned keystore.
Hi GCS,
Currently we have a keystore that we cannot open to verify certs and the expiry dates due to passord is unknown. We can confirm that the jdks' C:\jdk1.7.0_51\jre\lib\security\cacert has the valid trusted cert. Would the Pega SOAP connect - https://soaservices.rms.nsw.gov.au/<Service Path> looks further for the cert in jdk's cacert if it cannot find the cert in the assigned keystore file below.
-
Like (0)
-
Share this page Facebook Twitter LinkedIn Email Copying... Copied!
Accepted Solution
Pegasystems Inc.
GB
Just an aside: if you want to see if you can recover your certificate from your keystore: you might still be able to do this.
The password for the keystore is encrypted against the rule; so can be decrypted without actually knowing it.
You will *not* be able to recoved any keypairs from the keystore (unless you have the password): but you should be able to recover the certificate contents.
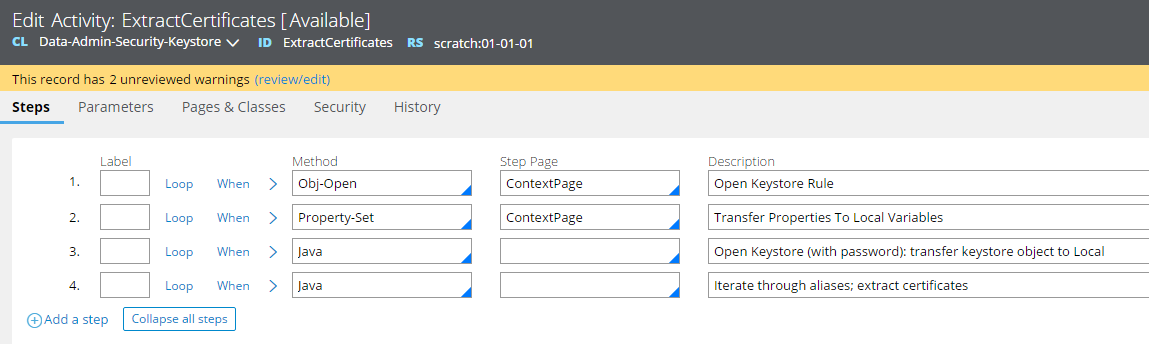
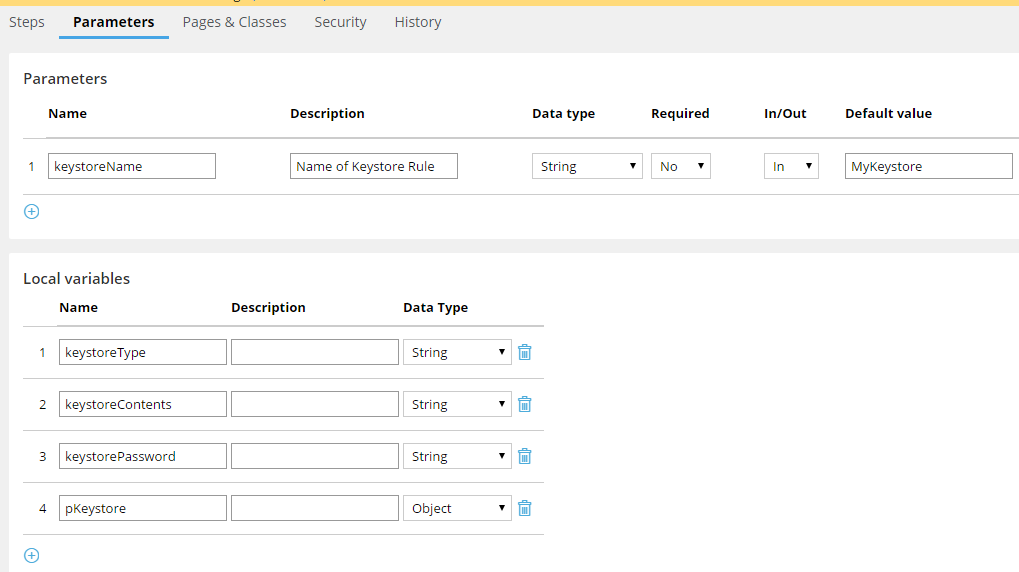
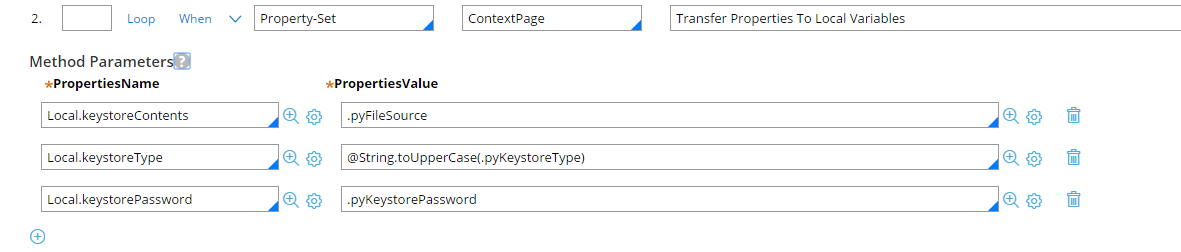
Here's an Activity to do that:
Just an aside: if you want to see if you can recover your certificate from your keystore: you might still be able to do this.
The password for the keystore is encrypted against the rule; so can be decrypted without actually knowing it.
You will *not* be able to recoved any keypairs from the keystore (unless you have the password): but you should be able to recover the certificate contents.
Here's an Activity to do that:
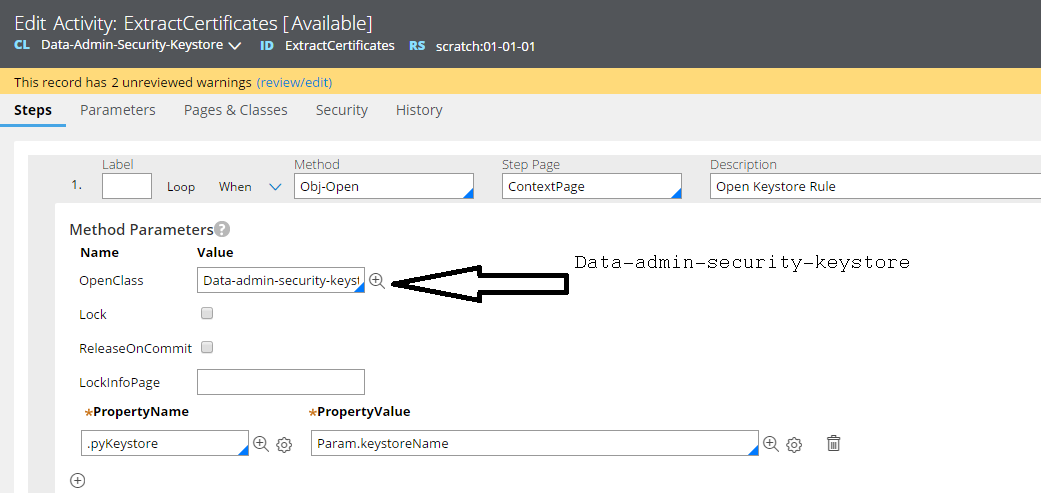
Java Step #3:
try {
java.security.KeyStore keystore= null;
java.security.Security.addProvider(new org.bouncycastle.jce.provider.BouncyCastleProvider());
if (keystoreType.equals("JKS") ) {
keystore = java.security.KeyStore.getInstance(keystoreType);
}
else {
if (keystoreType.equals("PKCS12") )
{
keystore = java.security.KeyStore.getInstance(keystoreType, "BC");
}
}
char KeyStorePassArray[] = tools.getPRCrypto().decrypt(keystorePassword).toCharArray();
byte[] buffer = Base64Util.decodeToByteArray(keystoreContents);
java.io.ByteArrayInputStream bis = new java.io.ByteArrayInputStream(buffer);
keystore.load(bis, KeyStorePassArray);
pKeystore=keystore;
}
catch(Exception e) { throw new PRRuntimeException(e); }
Java Step #4:
java.security.KeyStore keystore=(java.security.KeyStore)pKeystore;
try {
java.util.Enumeration en = keystore.aliases();
while(en.hasMoreElements()) {
String elementName = en.nextElement().toString();
if ( keystore.isCertificateEntry(elementName) ) {
java.security.cert.X509Certificate cert=(java.security.cert.X509Certificate)keystore.getCertificate(elementName);
oLog.infoForced( cert.toString() );
}
}
}
catch(Exception e) { throw new PRRuntimeException(e); }
The output currently just writes the text fields of the certs to the PegaRules log: you could alter this to (say) base64 encode to PEM format etc - and set up PRPC properties or whatever.
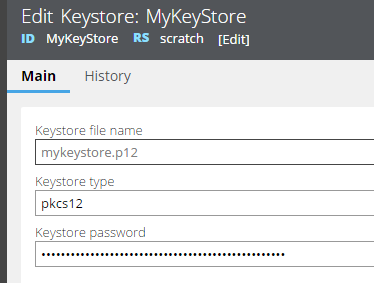
Here's the example output from my keystore 'mykeystore' (which I uploaded with a single certificate only - the one from the Mesh Site):
2016-02-01 18:21:32,774 [http-bio-7190-exec-3] [ STANDARD] [ ] [ scratch:01.01.01] (Admin_Security_Keystore.Action) INFO prpchost|xx.xx.xx.xx Admin@GCS - [0] Version: 3 SerialNumber: 10735574782033346628
IssuerDN: C=US,ST=Arizona,L=Scottsdale,O=GoDaddy.com\, Inc.,OU=http://certs.godaddy.com/repository/,CN=Go Daddy Secure Certificate Authority - G2
Start Date: Wed Mar 25 23:35:38 GMT 2015
Final Date: Thu Nov 15 21:17:45 GMT 2018
SubjectDN: OU=Domain Control Validated,CN=mesh.pega.com
Public Key: RSA Public Key
modulus: d86ab8e48544e4f5d74e1cf1784af6ce9080b527772f6d8147e03c62724380022c52237aa19137d227b32af1448761df4a456cd64c11714001e0dc57426ea1cf2ec4ab319913a1a5ba7214661109c516501c8584d0456084e66fa0b906cf1b33e95d607801eb1fe0fe64b498507cc7269a0c191e0daa34d4bc4031d93121ad2e6e9b5222c429e4c5dda0006625318e81c30436c3a0db403ff4db48117d2e6ff34d9904b4e6627fe641ca249a8b4a9f7f4d112c9c7e174369434a2367c3d13caa68c904becff7fa13e7a637ba48ef4c1ea5c87ae00242353ec768d7198c6527e397fb28e0c0bc47b840c4852e17a0a45931ce2351630b6106daba0fbaa51e2b316433be1ad4cabb233c490e70f1dbb5a7214bbb89c4c6f0cfb757da8db6ddc849e92429abd472f09b4d37b97dd5b86bf66636e51dd8df2478299309f80ae52a6d436603598267c7e0995421884988d158350a00b66c5bf4f19bfe70a955324d323794bc97a41fd67f66a1631e7ddfd0e548b91a8dd1f833da50a4ef2b791526d88f521caef9be4f6edc142bbe57dbb97634aed196e5c61bcae810093882e08d6826e5b86137acb9893d0194410f5337a0665b672b34969dd0db33a8d7eec0d6d8dc8167b2154b5b78471be35654dd712871da440ba8f0ee9ff3a234b0151b2c1f22b4e33d8ca30f030cee820736946bfb0737fe8a5932bb9d1abae34d81f5bd05
public exponent: 10001
Signature Algorithm: SHA256WITHRSA
Signature: 968178b85d3003d5be4074ea546e30e327b1f9fd
2aae11f685c0a80ebc6127b10d714c6915ff2459
93ca6ca34d19e99eda982ade995a3e8edd189070
83eea8eb19dfa06cc0a5e86185b769a37f656c6e
90b5aa7a6033d8f55da59207f43d56f86d0bde3c
fb4268ae79e1cc1a8c234d3c050cd9aebca0aeb2
89cd35e8364685e91215555914cc9c911ada4a3c
52d23f3c6f4fb618bb9bfc518ac1e1431c36d59c
26f175c3b103b28af6e0a9d5c3a1c76b6b002e35
98c1ee18fde4558f9c55d85e517b288856229721
5e7be20e76244e60439dd554f3f25764d770fb8c
39f9cec751d03ce47706892e50b9d3741bf9c9e0
e8b2466ff81880656777c17746d18b65
Extensions:
critical(true) BasicConstraints: isCa(false)
critical(false) Proprietary information hidden value = Sequence
ObjectIdentifier( Proprietary information hidden. Proprietary information hidden.1)
ObjectIdentifier( Proprietary information hidden. Proprietary information hidden.2)
[...]
I stole adapted the code mostly from the OOTB Activity 'getCertificate'.
Pegasystems Inc.
CA
Which version of Pega are you using? What's the app server? Anyway, if you want Pega to use the platform default truststore, why do you have truststore configured for the SOAP connector?
Pegasystems Inc.
AU
Hi Praneeth,
The Pega is 7.1.7 on Tomcat 7.0.52.
I am not sure of the history and so I don't know what is in the configured truststore. Anyhow if we are to use the JDK cacert, should I do one of the options below
1. Import this in the JDK truststore into the configuration for the SOAP connector? or
2. leave this blank? if so will it looks for the cacert as a fallback.
Regards
Seri
Pegasystems Inc.
CA
I would suggest that you go with option 2. Don't configure a truststore for your SOAP connector.
Pegasystems Inc.
AU
Thanks, just to confirm if do NOT configure the truststore for the soap connector, will it fall back to the JDK's cacert?
Regards
Seri
Pegasystems Inc.
CA
Yes, it should fall back to JDK's cacerts.
Pegasystems Inc.
GB
Hi Seri,
Just double-checking here: you quoted the path for 'cacerts' as the following:
C:\jdk1.7.0_51\jre\lib\security\cacert
But actually it should be 'cacerts' (plural) :
C:\jdk1.7.0_51\jre\lib\security\cacerts
This is probably just a typo in the Post: but just wanted to check in case this was the reason your certificate couldn't be found....
Cheers
John
Updated: 1 Feb 2016 17:15 EST
Pegasystems Inc.
AU
Yes, sorry that is right. it is the JDK C:\jdk1.7.0_51\jre\lib\security\cacerts. Plus, the same configured keystore file is used also for other services, to me it is best to see what are the certs inside that might be expired.
Quick question: When a cert is expired, normally transport layer is still encrypted e.g. on the browser I think you will see the waning. Would this break (exception occurs) the soap connection / service in Pega if the cert used expired, or would invalid cert reported in the log file and the encryption still take effect.
Cheers
Seri
Accepted Solution
Pegasystems Inc.
GB
Just an aside: if you want to see if you can recover your certificate from your keystore: you might still be able to do this.
The password for the keystore is encrypted against the rule; so can be decrypted without actually knowing it.
You will *not* be able to recoved any keypairs from the keystore (unless you have the password): but you should be able to recover the certificate contents.
Here's an Activity to do that:
Just an aside: if you want to see if you can recover your certificate from your keystore: you might still be able to do this.
The password for the keystore is encrypted against the rule; so can be decrypted without actually knowing it.
You will *not* be able to recoved any keypairs from the keystore (unless you have the password): but you should be able to recover the certificate contents.
Here's an Activity to do that:
Java Step #3:
try {
java.security.KeyStore keystore= null;
java.security.Security.addProvider(new org.bouncycastle.jce.provider.BouncyCastleProvider());
if (keystoreType.equals("JKS") ) {
keystore = java.security.KeyStore.getInstance(keystoreType);
}
else {
if (keystoreType.equals("PKCS12") )
{
keystore = java.security.KeyStore.getInstance(keystoreType, "BC");
}
}
char KeyStorePassArray[] = tools.getPRCrypto().decrypt(keystorePassword).toCharArray();
byte[] buffer = Base64Util.decodeToByteArray(keystoreContents);
java.io.ByteArrayInputStream bis = new java.io.ByteArrayInputStream(buffer);
keystore.load(bis, KeyStorePassArray);
pKeystore=keystore;
}
catch(Exception e) { throw new PRRuntimeException(e); }
Java Step #4:
java.security.KeyStore keystore=(java.security.KeyStore)pKeystore;
try {
java.util.Enumeration en = keystore.aliases();
while(en.hasMoreElements()) {
String elementName = en.nextElement().toString();
if ( keystore.isCertificateEntry(elementName) ) {
java.security.cert.X509Certificate cert=(java.security.cert.X509Certificate)keystore.getCertificate(elementName);
oLog.infoForced( cert.toString() );
}
}
}
catch(Exception e) { throw new PRRuntimeException(e); }
The output currently just writes the text fields of the certs to the PegaRules log: you could alter this to (say) base64 encode to PEM format etc - and set up PRPC properties or whatever.
Here's the example output from my keystore 'mykeystore' (which I uploaded with a single certificate only - the one from the Mesh Site):
2016-02-01 18:21:32,774 [http-bio-7190-exec-3] [ STANDARD] [ ] [ scratch:01.01.01] (Admin_Security_Keystore.Action) INFO prpchost|xx.xx.xx.xx Admin@GCS - [0] Version: 3 SerialNumber: 10735574782033346628
IssuerDN: C=US,ST=Arizona,L=Scottsdale,O=GoDaddy.com\, Inc.,OU=http://certs.godaddy.com/repository/,CN=Go Daddy Secure Certificate Authority - G2
Start Date: Wed Mar 25 23:35:38 GMT 2015
Final Date: Thu Nov 15 21:17:45 GMT 2018
SubjectDN: OU=Domain Control Validated,CN=mesh.pega.com
Public Key: RSA Public Key
modulus: d86ab8e48544e4f5d74e1cf1784af6ce9080b527772f6d8147e03c62724380022c52237aa19137d227b32af1448761df4a456cd64c11714001e0dc57426ea1cf2ec4ab319913a1a5ba7214661109c516501c8584d0456084e66fa0b906cf1b33e95d607801eb1fe0fe64b498507cc7269a0c191e0daa34d4bc4031d93121ad2e6e9b5222c429e4c5dda0006625318e81c30436c3a0db403ff4db48117d2e6ff34d9904b4e6627fe641ca249a8b4a9f7f4d112c9c7e174369434a2367c3d13caa68c904becff7fa13e7a637ba48ef4c1ea5c87ae00242353ec768d7198c6527e397fb28e0c0bc47b840c4852e17a0a45931ce2351630b6106daba0fbaa51e2b316433be1ad4cabb233c490e70f1dbb5a7214bbb89c4c6f0cfb757da8db6ddc849e92429abd472f09b4d37b97dd5b86bf66636e51dd8df2478299309f80ae52a6d436603598267c7e0995421884988d158350a00b66c5bf4f19bfe70a955324d323794bc97a41fd67f66a1631e7ddfd0e548b91a8dd1f833da50a4ef2b791526d88f521caef9be4f6edc142bbe57dbb97634aed196e5c61bcae810093882e08d6826e5b86137acb9893d0194410f5337a0665b672b34969dd0db33a8d7eec0d6d8dc8167b2154b5b78471be35654dd712871da440ba8f0ee9ff3a234b0151b2c1f22b4e33d8ca30f030cee820736946bfb0737fe8a5932bb9d1abae34d81f5bd05
public exponent: 10001
Signature Algorithm: SHA256WITHRSA
Signature: 968178b85d3003d5be4074ea546e30e327b1f9fd
2aae11f685c0a80ebc6127b10d714c6915ff2459
93ca6ca34d19e99eda982ade995a3e8edd189070
83eea8eb19dfa06cc0a5e86185b769a37f656c6e
90b5aa7a6033d8f55da59207f43d56f86d0bde3c
fb4268ae79e1cc1a8c234d3c050cd9aebca0aeb2
89cd35e8364685e91215555914cc9c911ada4a3c
52d23f3c6f4fb618bb9bfc518ac1e1431c36d59c
26f175c3b103b28af6e0a9d5c3a1c76b6b002e35
98c1ee18fde4558f9c55d85e517b288856229721
5e7be20e76244e60439dd554f3f25764d770fb8c
39f9cec751d03ce47706892e50b9d3741bf9c9e0
e8b2466ff81880656777c17746d18b65
Extensions:
critical(true) BasicConstraints: isCa(false)
critical(false) Proprietary information hidden value = Sequence
ObjectIdentifier( Proprietary information hidden. Proprietary information hidden.1)
ObjectIdentifier( Proprietary information hidden. Proprietary information hidden.2)
[...]
I stole adapted the code mostly from the OOTB Activity 'getCertificate'.
Updated: 2 Feb 2016 3:11 EST
Pegasystems Inc.
AU
Hi John,
I am getting the error... with PFX file, but works with JKS file. I believe the server JRE has the US's UnlimitedJCEPolicyJD installed.
Caused by: java.io.IOException: exception unwrapping private key - java.security.InvalidKeyException: Illegal key size
at org.bouncycastle.jcajce.provider.keystore.pkcs12.PKCS12KeyStoreSpi.unwrapKey(Unknown Source)
at org.bouncycastle.jcajce.provider.keystore.pkcs12.PKCS12KeyStoreSpi.engineLoad(Unknown Source)
at java.security.KeyStore.load(KeyStore.java:1214)
at com.pegarules.generated.activity.sh_action_scextractcerts_9382c8f7d3922168dfc1c637b11f4d02.step3_circum0(sh_action_scextractcerts_9382c8f7d3922168dfc1c637b11f4d02.java:347)
... 60 more
In fact, when I just simply clicked on "Save" again on the Keystore in Pega, you already get the error. I think this could be a bug in Pega to save PKCS12 file?
2016-02-02 18:59:06,889 [ http-apr-80-exec-80] [TABTHREAD4] [ ] [ IMS:01.10.01] (Admin_Security_Keystore.Action) ERROR xxxxx charoes - Unable to open Keystore java.security.KeyStore@7b8b1d7d:
java.io.IOException: exception unwrapping private key - java.security.InvalidKeyException: Illegal key size
Hi John,
I am getting the error... with PFX file, but works with JKS file. I believe the server JRE has the US's UnlimitedJCEPolicyJD installed.
Caused by: java.io.IOException: exception unwrapping private key - java.security.InvalidKeyException: Illegal key size
at org.bouncycastle.jcajce.provider.keystore.pkcs12.PKCS12KeyStoreSpi.unwrapKey(Unknown Source)
at org.bouncycastle.jcajce.provider.keystore.pkcs12.PKCS12KeyStoreSpi.engineLoad(Unknown Source)
at java.security.KeyStore.load(KeyStore.java:1214)
at com.pegarules.generated.activity.sh_action_scextractcerts_9382c8f7d3922168dfc1c637b11f4d02.step3_circum0(sh_action_scextractcerts_9382c8f7d3922168dfc1c637b11f4d02.java:347)
... 60 more
In fact, when I just simply clicked on "Save" again on the Keystore in Pega, you already get the error. I think this could be a bug in Pega to save PKCS12 file?
2016-02-02 18:59:06,889 [ http-apr-80-exec-80] [TABTHREAD4] [ ] [ IMS:01.10.01] (Admin_Security_Keystore.Action) ERROR xxxxx charoes - Unable to open Keystore java.security.KeyStore@7b8b1d7d:
java.io.IOException: exception unwrapping private key - java.security.InvalidKeyException: Illegal key size
I have posted a separate issue for product support at Saving PKCS12 resulted in Error in the log file
Regards
Seri
Updated: 2 Feb 2016 5:35 EST
Pegasystems Inc.
GB
Hi Seri,
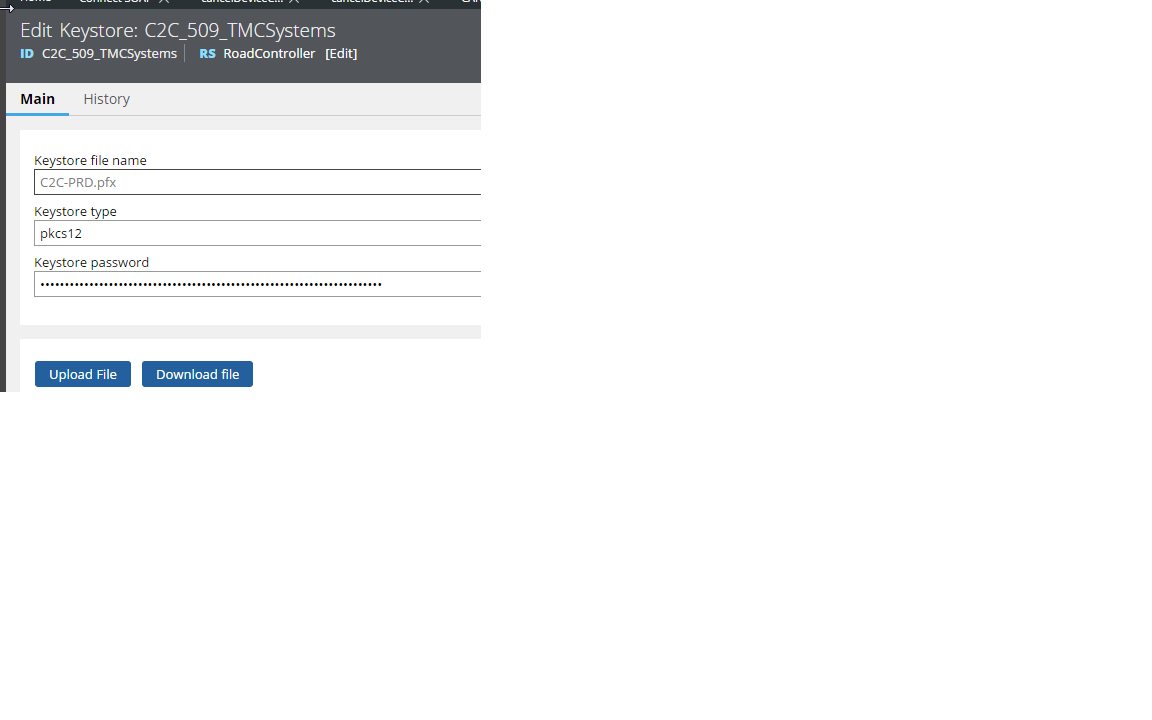
I also tested with 'pkcs12' keystore - it works on my system. I have attached the file for reference. (password 'topsecret').
Perhaps the password was saved incorrectly on the keystore rule ?
Try the following maybe:
1. Use the 'Download file' button - to save a local copy outside of PRPC.
2. Modify the Activity I provided to echo out the stored Password.
2. Use 'Keystore Explorer' [ http://keystore-explorer.org/ ] (or the tool of your choice) to open the keystore using the result of 2
Does this work ? If not: the password must be wrong; or else the keystore is corrupt (or flagged as the wrong type ?)
Updated: 2 Feb 2016 21:09 EST
Pegasystems Inc.
AU
Hi John,
1. it is indeed the US JCE restriction policy jar that is somehow not in the default PRPC PE. I would have thought the PE with self-contained JRE has the US Policy Jar in place.
2. I can confirm the client JDK/JRE also not patched. I will get them to patch.
Thanks for your help...
Seri