Question
Pegasystems Inc.
JP
Last activity: 26 May 2021 5:06 EDT
"Unable to execute OIDC flow: Cautht exception while parsing that id token" is thrown with OpenID Connect authentication
Hi,
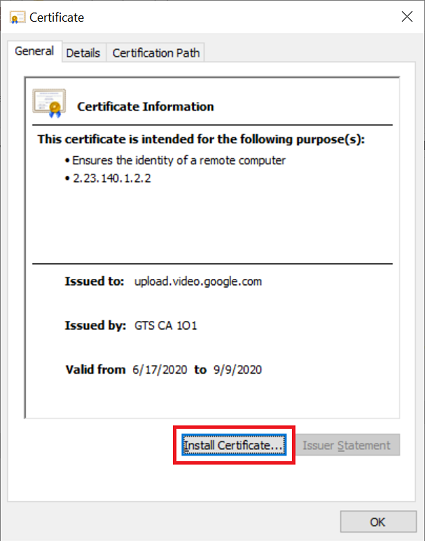
I've created an Authentication Service for OpenID Connect. After configuration, when I access Pega URL, it gets redirected to OP (OpenID Provider). There I enter credentials, and it tries to redirect back to Pega, but below error screen shows up on browser.
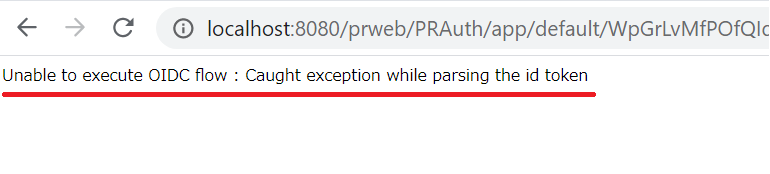
"Unable to execute OIDC flow : Cautht exception while parsing that id token"
For your information, I am positive that the settings in Authentication Service rule form are correct, and there shouldn't be anything wrong with OP's settings either. The reason I say so is because the same settings work in another laptop (let's call this "laptop1"). I tried Google Identity Platform, and also KeyCloak for OP and both are working fine with laptop1, while both don't work with laptop2. This proves that at least settings in both OP and RP (PRPC) side are correct.
I am not sure what exactly is different between my laptop1 (working) and laptop2 (not working), but sometimes laptop2 throws SSLHandShakeException too, so something could be wrong with SSL? Do I need to do anything with certification? Both laptop1 and laptop2 are not SSL enabled, and I am using only HTTP (8080) for Tomcat.
Hi,
I've created an Authentication Service for OpenID Connect. After configuration, when I access Pega URL, it gets redirected to OP (OpenID Provider). There I enter credentials, and it tries to redirect back to Pega, but below error screen shows up on browser.

"Unable to execute OIDC flow : Cautht exception while parsing that id token"
For your information, I am positive that the settings in Authentication Service rule form are correct, and there shouldn't be anything wrong with OP's settings either. The reason I say so is because the same settings work in another laptop (let's call this "laptop1"). I tried Google Identity Platform, and also KeyCloak for OP and both are working fine with laptop1, while both don't work with laptop2. This proves that at least settings in both OP and RP (PRPC) side are correct.
I am not sure what exactly is different between my laptop1 (working) and laptop2 (not working), but sometimes laptop2 throws SSLHandShakeException too, so something could be wrong with SSL? Do I need to do anything with certification? Both laptop1 and laptop2 are not SSL enabled, and I am using only HTTP (8080) for Tomcat.
I set logging level for OIDCClientHandler as DEBUG - below are the PegaRULES log files for two laptops. I extracted only important messages for the readability.
- Laptop1 (working machine)
DEBUG localhost| Proprietary information hidden - Initiating OIDC flow
DEBUG localhost| Proprietary information hidden - Constructing authorization URL for OIDC provider
DEBUG localhost| Proprietary information hidden - Constructed authorization URL for OIDC provider : https://accounts.google.com/o/oauth2/auth?redirect_uri=http%3A%2F%2Flocalhost%3A8080%2Fprweb%2FPRAuth&client_id=18549103960-lrolt331lf7u1ei6tsirmpffg1ih6hrq.apps.googleusercontent.com&scope=openid profile email &state=b14e874ac059a638cce69be41e16d40878bb35bf13876f54f3dac9cb46ddb662app/default&nonce=eb66948bb55d02f6b727e488d1673bbea97aeeb3c857d112ebd5a4818209b128&response_type=code
DEBUG localhost| Proprietary information hidden - Processing authorization code recieved from OIDC provider
DEBUG localhost| Proprietary information hidden - StateParam Validation is successful
DEBUG localhost| Proprietary information hidden - Fetching access token using authCode received
DEBUG localhost| Proprietary information hidden - Successfully fetched accesss token and ID token using authCode
DEBUG localhost| Proprietary information hidden - Validating ID token received from access token end point eyJhbGciOiJSUzI1NiIsImtpZCI6ImE0MWEzNTcwYjhlM2FlMWI3MmNhYWJjYWE3YjhkMmRiMjA2NWQ3YzEiLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJhY2NvdW50cy5nb29nbGUuY29tIiwiYXpwIjoiMTg1NDkxMDM5NjAtbHJvbHQzMzFsZjd1MWVpNnRzaXJtcGZmZzFpaDZocnEuYXBwcy5nb29nbGV1c2VyY29udGVudC5jb20iLCJhdWQiOiIxODU0OTEwMzk2MC1scm9sdDMzMWxmN3UxZWk2dHNpcm1wZmZnMWloNmhycS5hcHBzLmdvb2dsZXVzZXJjb250ZW50LmNvbSIsInN1YiI6IjEwNDIxOTgyMjcxMzYxMTUwOTc3MiIsImVtYWlsIjoicGVnYS5qYXBhbkBnbWFpbC5jb20iLCJlbWFpbF92ZXJpZmllZCI6dHJ1ZSwiYXRfaGFzaCI6IjBxbWtFeGlrN05LZEo3RTRiNXJ2TXciLCJub25jZSI6ImViNjY5NDhiYjU1ZDAyZjZiNzI3ZTQ4OGQxNjczYmJlYTk3YWVlYjNjODU3ZDExMmViZDVhNDgxODIwOWIxMjgiLCJpYXQiOjE1OTM1MTg3ODYsImV4cCI6MTU5MzUyMjM4Nn0.IE7Hs73u3tuS6EDE4cyISHFcCnK-879CTr1o2oano2iA0esXwJaqn9dGLU2TGt3b0CEQzGX2OT7aWCNAhrEU4W2ULtovQ75uNJ2XR9iS-70oHI585204s3sYbg6z4kMctIo0fbroUrJ2sJHzt5gMczr-mj53kCURyRny9WNHWmyEQTysnf1HyITLaCOyelR9fk1ONbjmD1_GTQ0L7fD_lfRl7Cj9n8IAHgWPzh9ki4By7oYdxYyMVv5oshS6lPdk_ZY34WpVLgEs-wkvxMJYHOuGQVm7ojG_pF9XrdWjYKQPp3Zj1rcCAbVFlcoxZj9CZyTJAkskWzg1xz3eSUbTzw
DEBUG localhost| Proprietary information hidden - Succesfully validated ID token with standard claims
DEBUG localhost| Proprietary information hidden - Retrieving userInfo claims from user info Endpoint
DEBUG localhost| Proprietary information hidden - Fetch operator from claim {email} from received ID token claims
DEBUG localhost| Proprietary information hidden - Succesfully established operator from received ID token claims
DEBUG localhost| Proprietary information hidden - Successfully authenticated operator with OIDC flow
- Laptop2 (not working machine)
DEBUG localhost| Proprietary information hidden - Initiating OIDC flow
DEBUG localhost| Proprietary information hidden - Constructing authorization URL for OIDC provider
DEBUG localhost| Proprietary information hidden - Constructed authorization URL for OIDC provider : https://accounts.google.com/o/oauth2/auth?redirect_uri=http%3A%2F%2Flocalhost%3A8080%2Fprweb%2FPRAuth&client_id=18549103960-lrolt331lf7u1ei6tsirmpffg1ih6hrq.apps.googleusercontent.com&scope=openid profile email &state=20002b9774d4ac07d45e62ef179c5ac281a68353ba57589f371dd33f6061fc10app/default&nonce=69e6099264451ef9be1139b7426fb98f1510011f536ded32f265e6b97774f5d2&response_type=code
DEBUG localhost| Proprietary information hidden - Processing authorization code recieved from OIDC provider
DEBUG localhost| Proprietary information hidden - StateParam Validation is successful
DEBUG localhost| Proprietary information hidden - Fetching access token using authCode received
DEBUG localhost| Proprietary information hidden - Successfully fetched accesss token and ID token using authCode
DEBUG localhost| Proprietary information hidden - Validating ID token received from access token end point eyJhbGciOiJSUzI1NiIsImtpZCI6ImE0MWEzNTcwYjhlM2FlMWI3MmNhYWJjYWE3YjhkMmRiMjA2NWQ3YzEiLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJhY2NvdW50cy5nb29nbGUuY29tIiwiYXpwIjoiMTg1NDkxMDM5NjAtbHJvbHQzMzFsZjd1MWVpNnRzaXJtcGZmZzFpaDZocnEuYXBwcy5nb29nbGV1c2VyY29udGVudC5jb20iLCJhdWQiOiIxODU0OTEwMzk2MC1scm9sdDMzMWxmN3UxZWk2dHNpcm1wZmZnMWloNmhycS5hcHBzLmdvb2dsZXVzZXJjb250ZW50LmNvbSIsInN1YiI6IjEwNDIxOTgyMjcxMzYxMTUwOTc3MiIsImVtYWlsIjoicGVnYS5qYXBhbkBnbWFpbC5jb20iLCJlbWFpbF92ZXJpZmllZCI6dHJ1ZSwiYXRfaGFzaCI6Ik4wdm14bGNwcXg3OHVFTHVBR3hUN1EiLCJub25jZSI6IjY5ZTYwOTkyNjQ0NTFlZjliZTExMzliNzQyNmZiOThmMTUxMDAxMWY1MzZkZWQzMmYyNjVlNmI5Nzc3NGY1ZDIiLCJpYXQiOjE1OTM1MjA4MTgsImV4cCI6MTU5MzUyNDQxOH0.f6mF6E0jKVOh6HXBOQcdBDQJE2xwwWDySDujsaRj5dFL--r2TlT5D6ZhJ1slrwJu53I5-51CPM5JBx4yeYU8u28AuH0icbUZBO4diMQsrKxMDRavUMYZUWHbmEgt2AglW7ceubqL98_r__uu2L_X-f-Ou1PxwjJFKU2AEbEy7bGu6GyRxW_J-ovDX1VVLJXsc-BGOVBxpn6KH7oqv9Z6RGJFjF6IEQmR21b3hQF58TDNfIl3bmYW233smLZ2zVK-57t49JgpBNqAC9-_1yvKpjdZpCgu7n-y1_GzIPktpjGpSRVvG6tHqjOIthNx4M1cfsJ3qYb8b9bmMxr1_yQFEQ
After validating ID token step, there was no log written. Isn't this weird?
Thanks,