SSL configuration for SOAP/REST connectors
Scenario 1: one-way SSL- only the client validates the endpoint server’s identity and the endopint server does not validate the client’s idendity
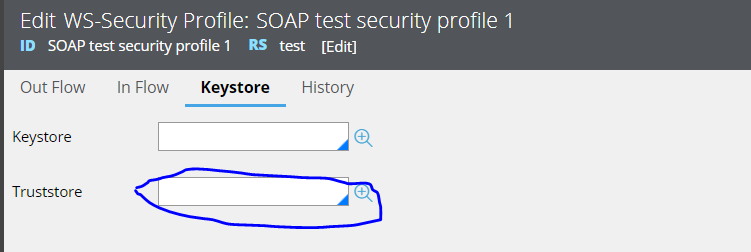
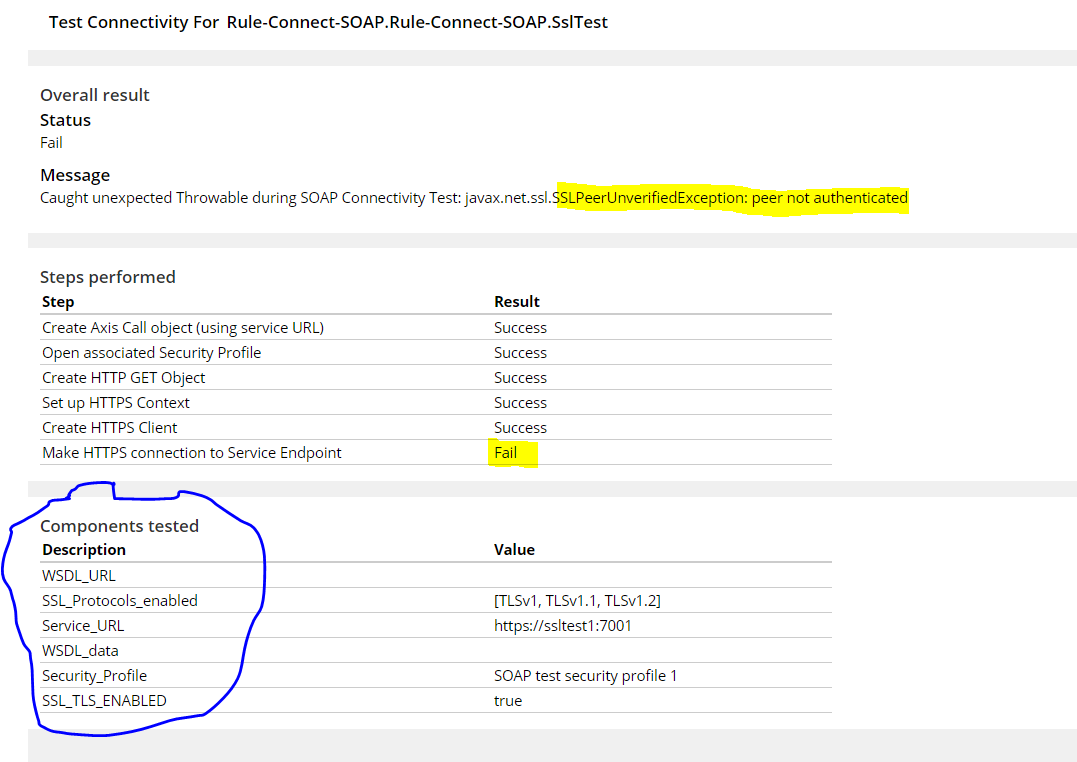
In this case, we need to have a truststore configured in connect-SOAP configuration and the SSL certificate of corresponding endpoint should be availabe in that truststore(JKS). As shown below, the connectivity will fail if the truststore is not configured.
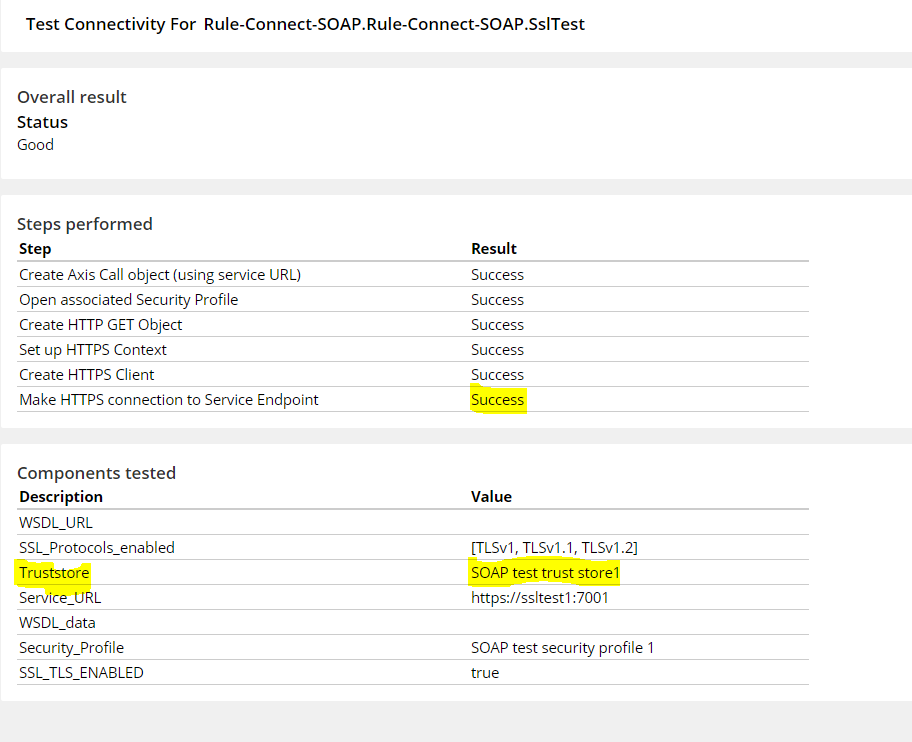
Valid configuration for one-way SSL
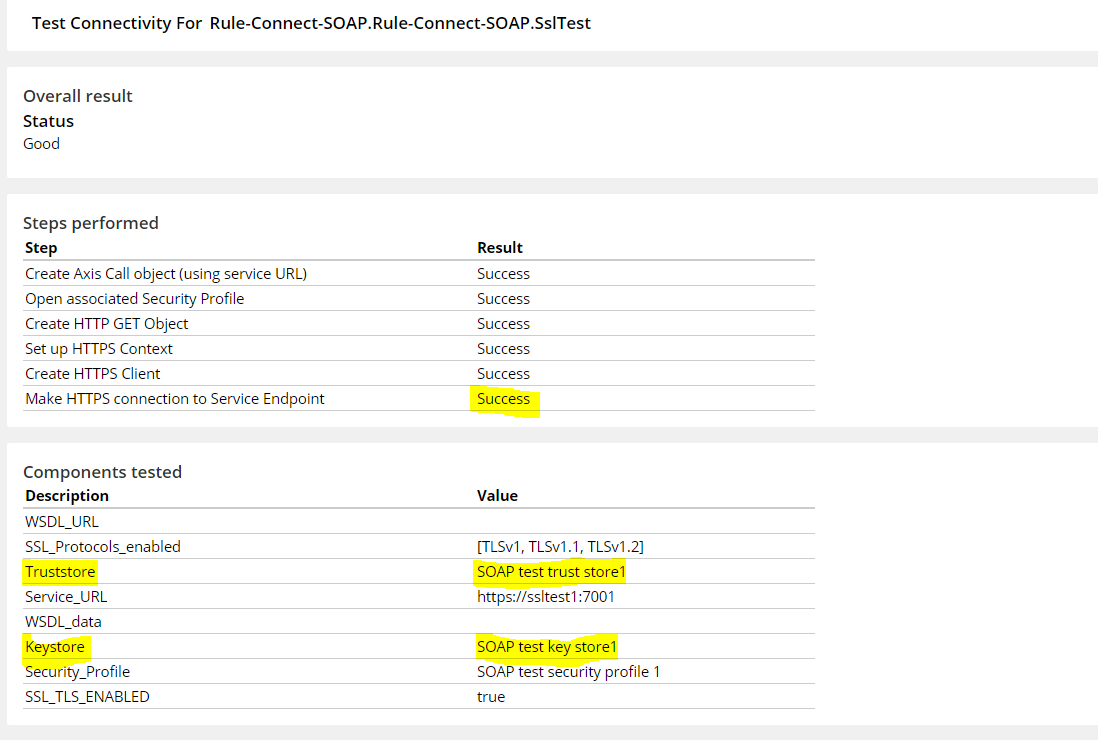
Test connectivity gives a success response when the trust store component is configured with appropriate SSL certificate.
Scenario 2: two-way SSL- Client validates the endpoint server’s identity and the endopint server validates the client’s idendity
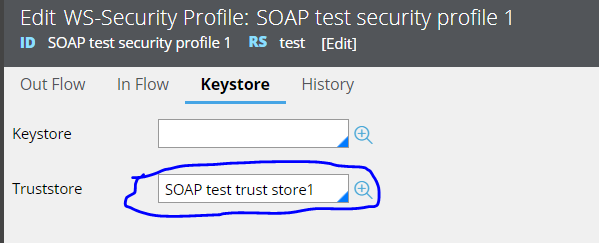
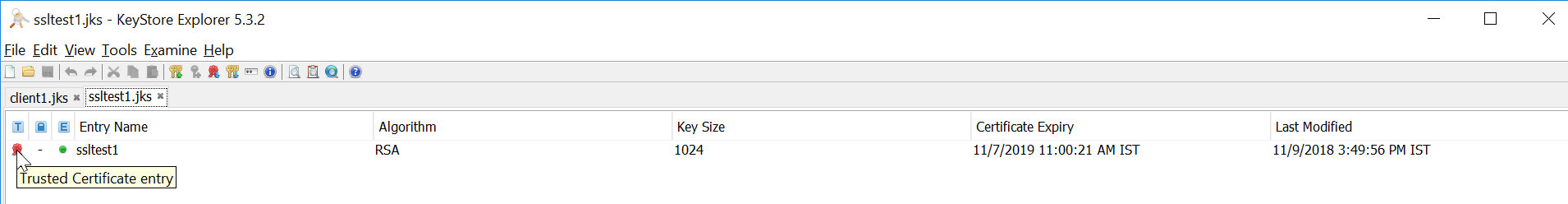
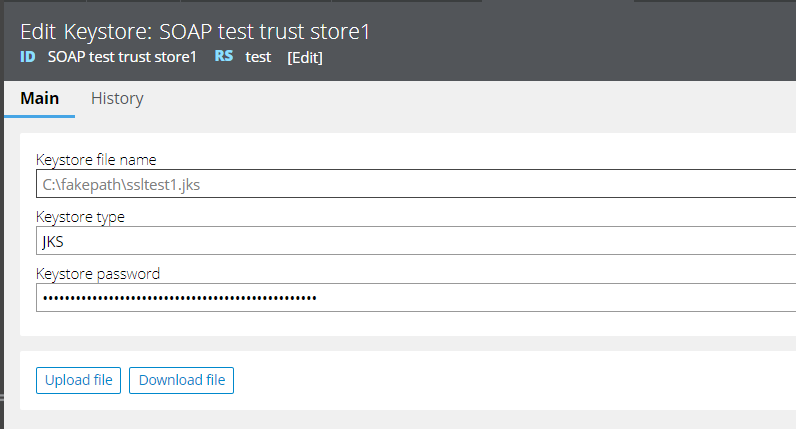
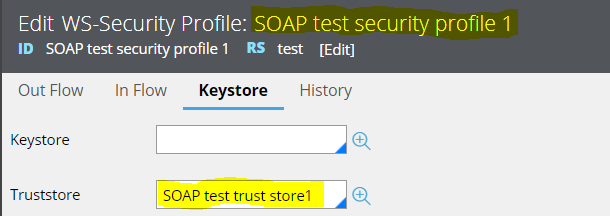
The endpoint server is configured with two-way SSL. So, connectivity to endpoint will fail if we do not configure the valid keystore parameter along with the truststore. As shown below, only the truststore is defined in SOAP connector configuration without keystore. So, the connectivity fails as expected.
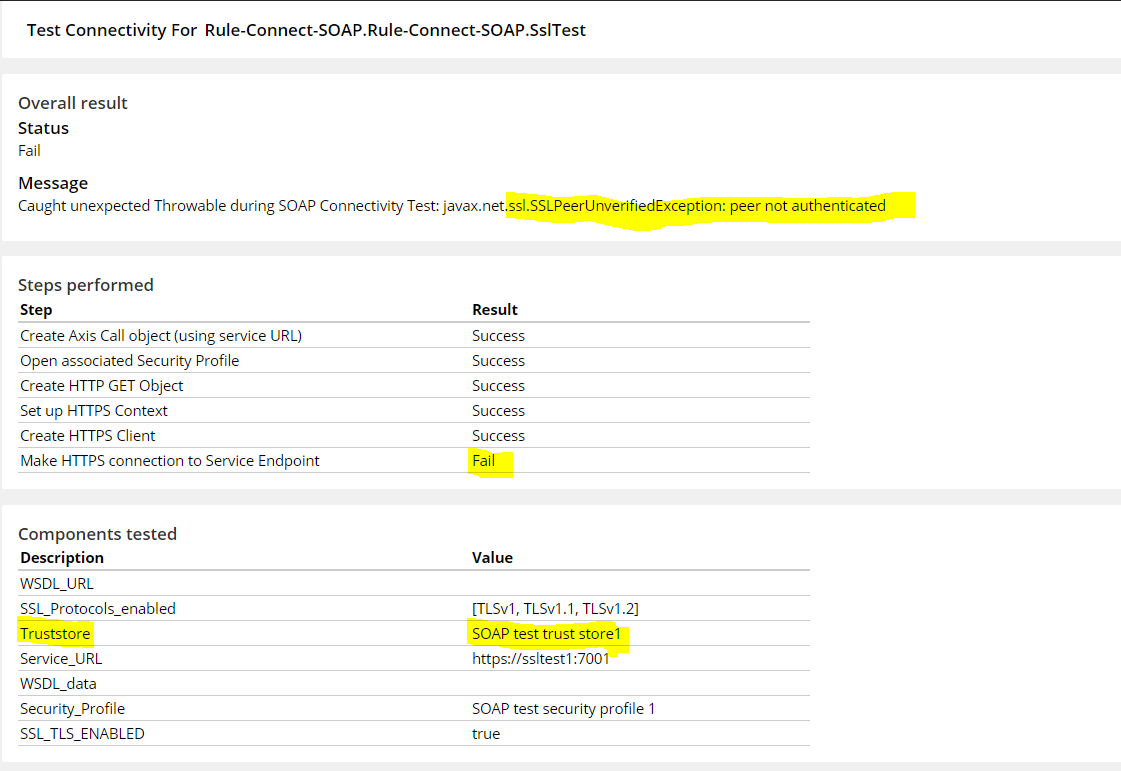
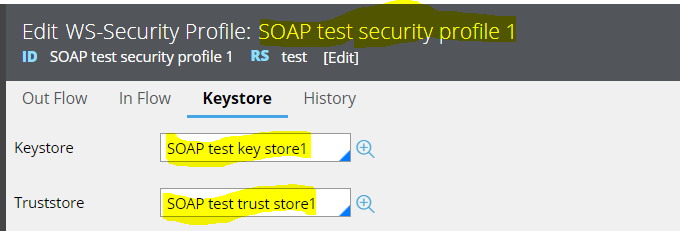
Valid configuration for two-way SSL
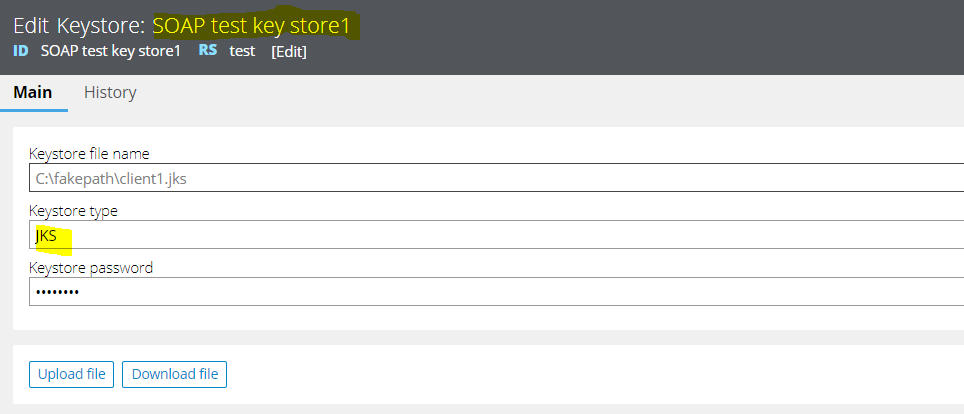
For the same scenario, truststore and keystore parameters are configured appropriately to facilitate the 2-way SSL communication and the test connectivity gives success response.
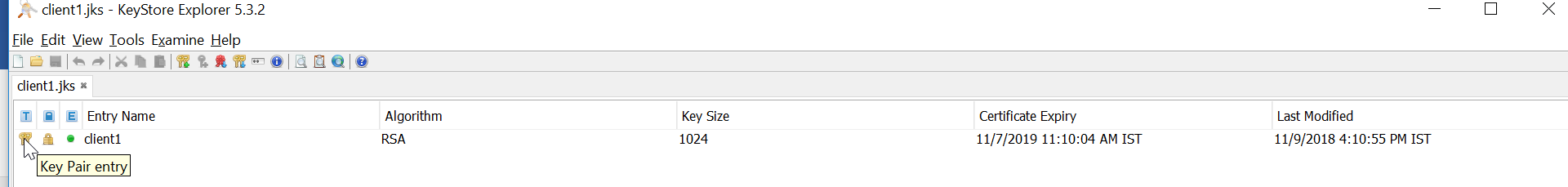
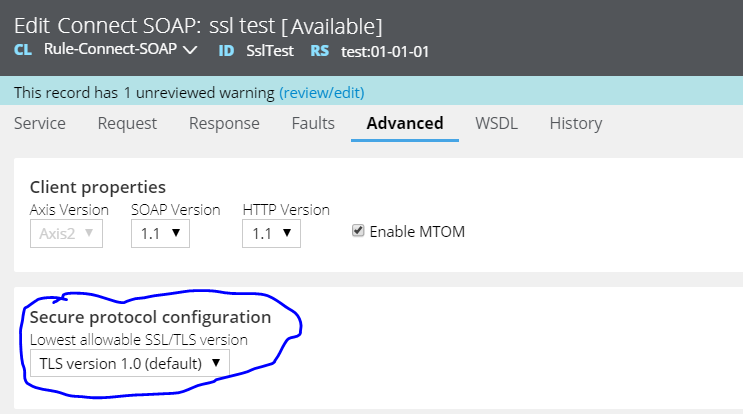
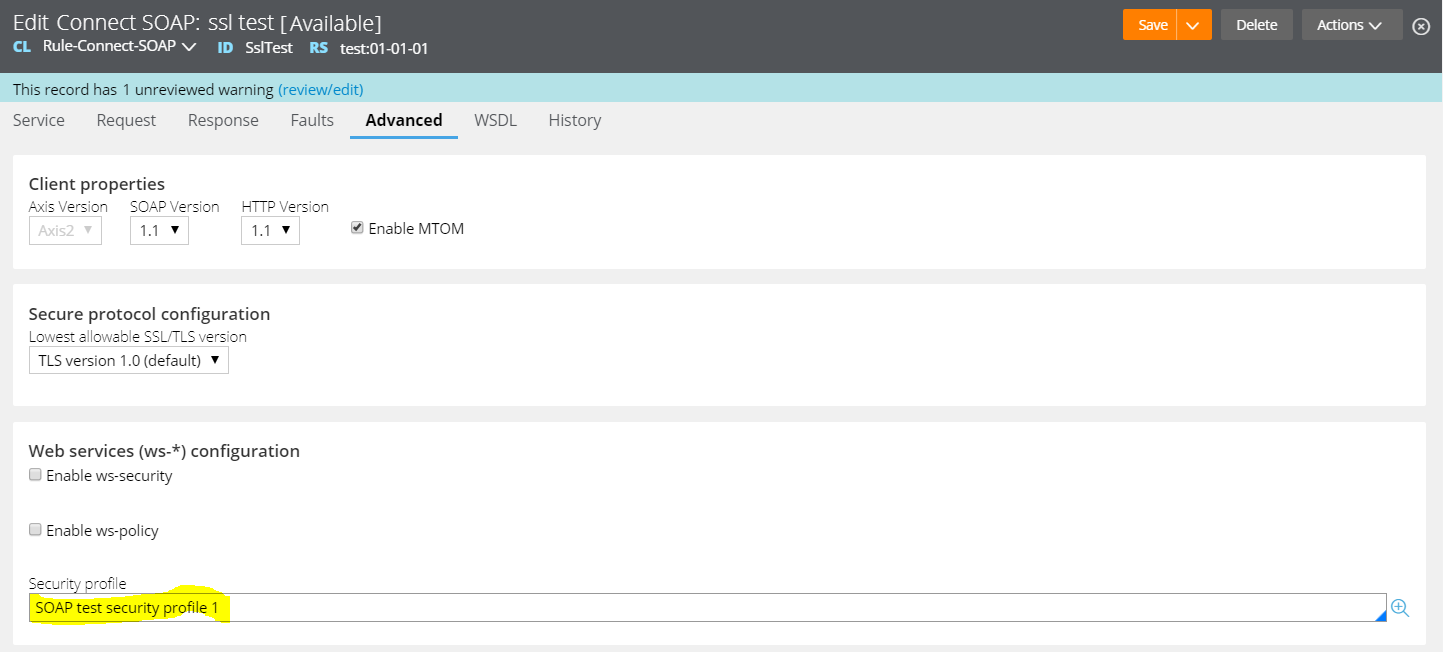
TLS configuration
As a standard practice, the endpoint server should be configured to support the latest TLS version. As of now, TLS 1.2 should be preferred one. If the endpoint supports TLS 1.2, then connect-SOAP/REST (client side) rule will work fine with any value (TLS 1.0,1.1 and 1.2). However, some old servers still serve with older TLS versions (TLS 1.0 and 1.1) possibly due to some dependency with the tools being used. In those cases, the SOAP connector must be configured with corresponding TLS version.
Note: TLS version configured in Connect-SOAP configuration is termed as “Lowest allowable SSL/TLS version”. Given below is the list of accepted TLS versions for the respective configuration.
|
Value of “Lowest allowable SSL/TLS version” parameter |
Accepted TLS version at client(pega) side |
Remarks |
|
SSL version 3 |
SSLv3, TLSv1.0, TLSv1.1, TLSv1.2 |
SSLv3 is deprecated, should not be used |
|
TLS version 1.0 |
TLSv1.0, TLSv1.1, TLSv1.2 |
|
|
TLS version 1.1 |
TLSv1.1, TLSv1.2 |
|
|
TLS version 1.2 |
TLSv1.2 |
Should be the preferred one |
TLS version mismatch
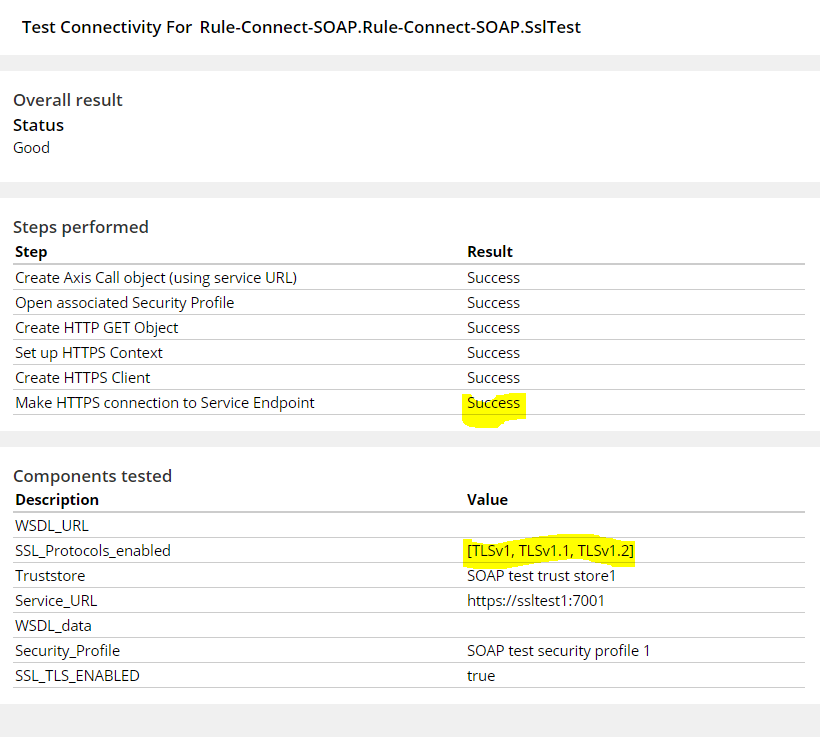
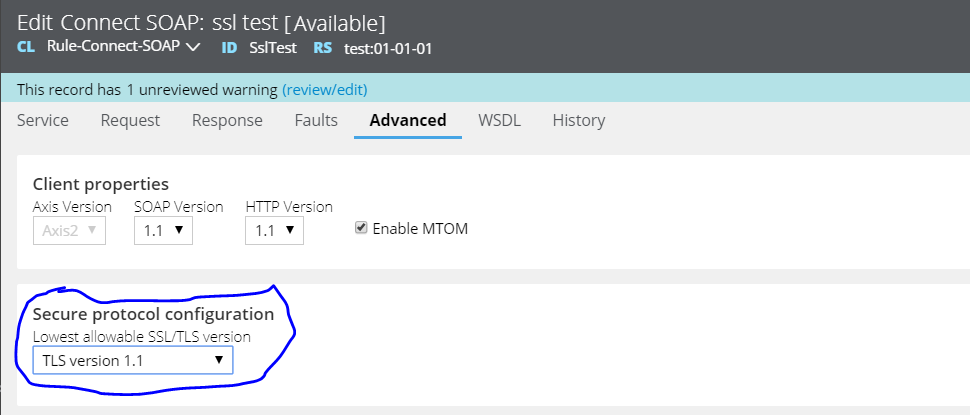
Test case 1: Connectivity Succeeds
TLS version at destination server-1.2
TLS version at source(pega)-1.1
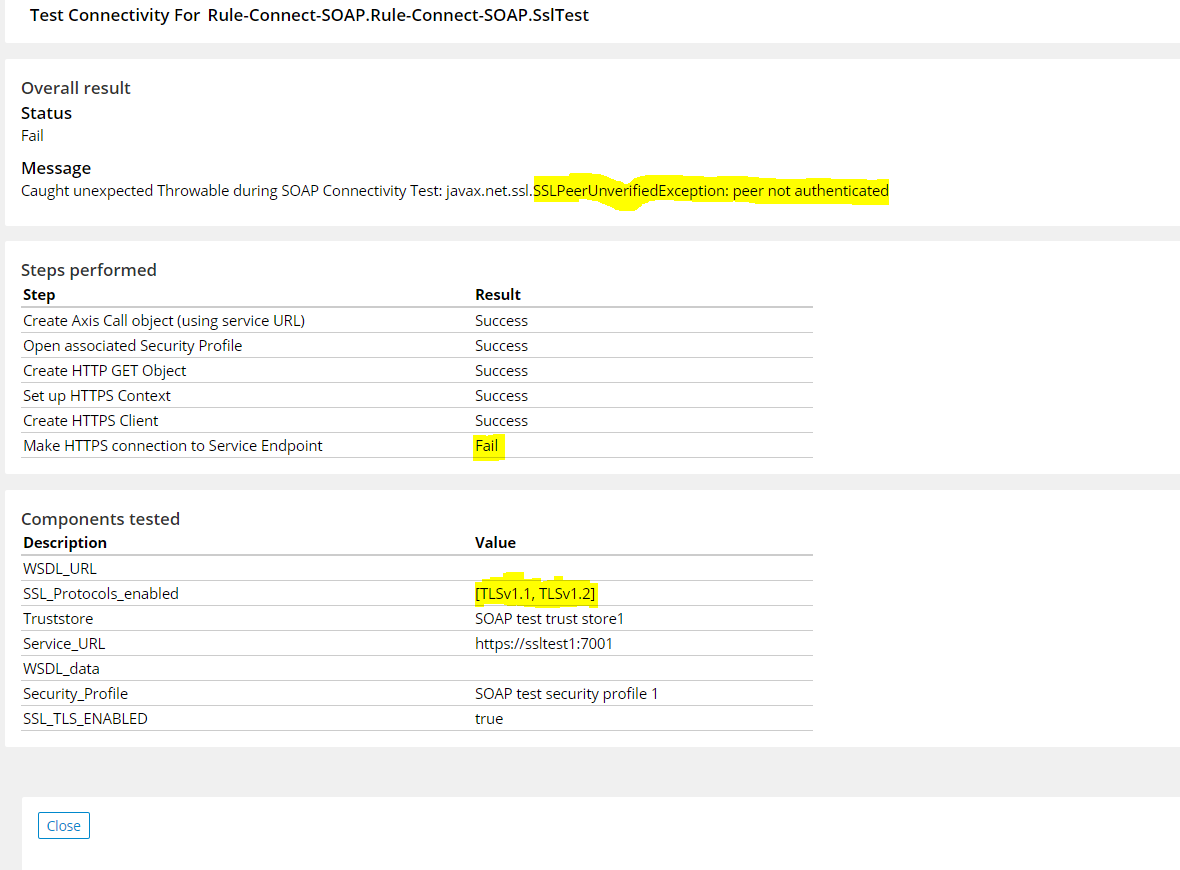
Test case 2: Connectivity Succeeds
TLS version at destination server-1.2
TLS version at source(pega)-1.2
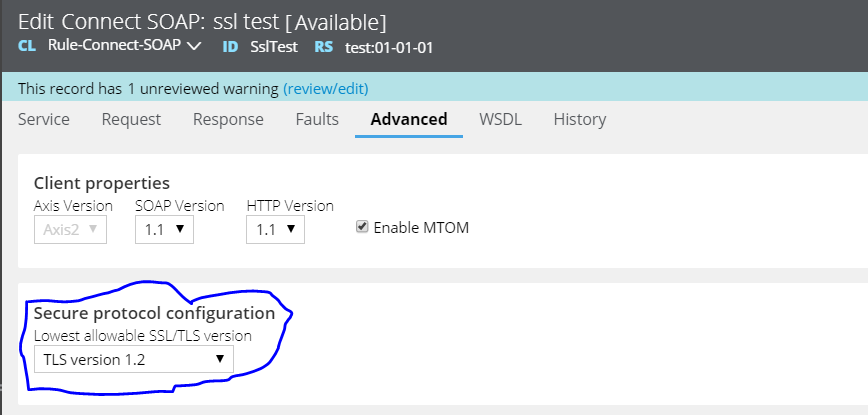
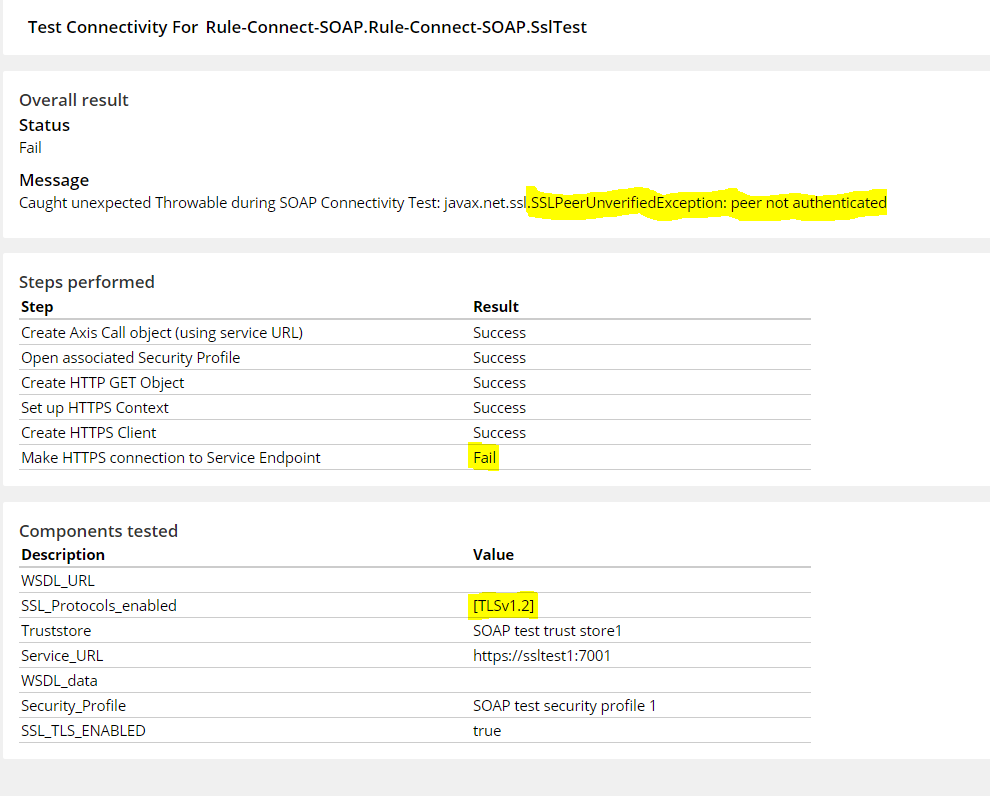
Test case 3: Connectivity Fails
TLS version at destination server-1.1
TLS version at source(pega)-1.2