Discussion
Pegasystems Inc.
JP
Last activity: 1 May 2023 12:23 EDT
OIDC session not terminated when logout
Hi,
My customer reported that OIDC (OpenID Connect) session is not terminated when user logs out from Pega. In this post, I will share what the issue is, and how we resolved it.
1. Symptoms
After end user logs out from Pega Platform and accesses SSO URL again, it is expected that system shows OP (OpenID Provider) log in screen for re-authentication. However, system just lets user log in without re-authentication process.
As you can see from above demo, system displays Pega's logout screen when user clicks log off. Then user accesses the SSO URL for the second time, log in process occurs without Okta credentials entry.
2. Root cause
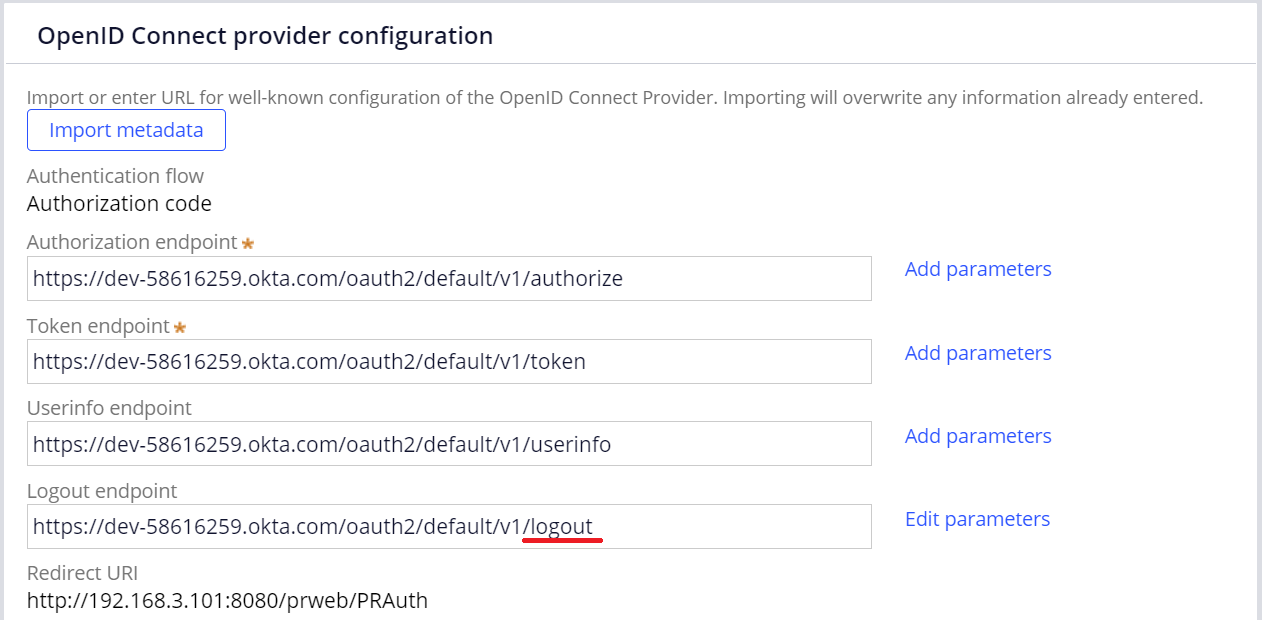
This is because you haven't configured logout endpoint marked below. Without this settings, OIDC session is not terminated and it is an expected behavior. This applies for not only Okta but any other OIDC software. Importing metadata populates all other endpoints, but not logout endpoint. You should set this up manually.
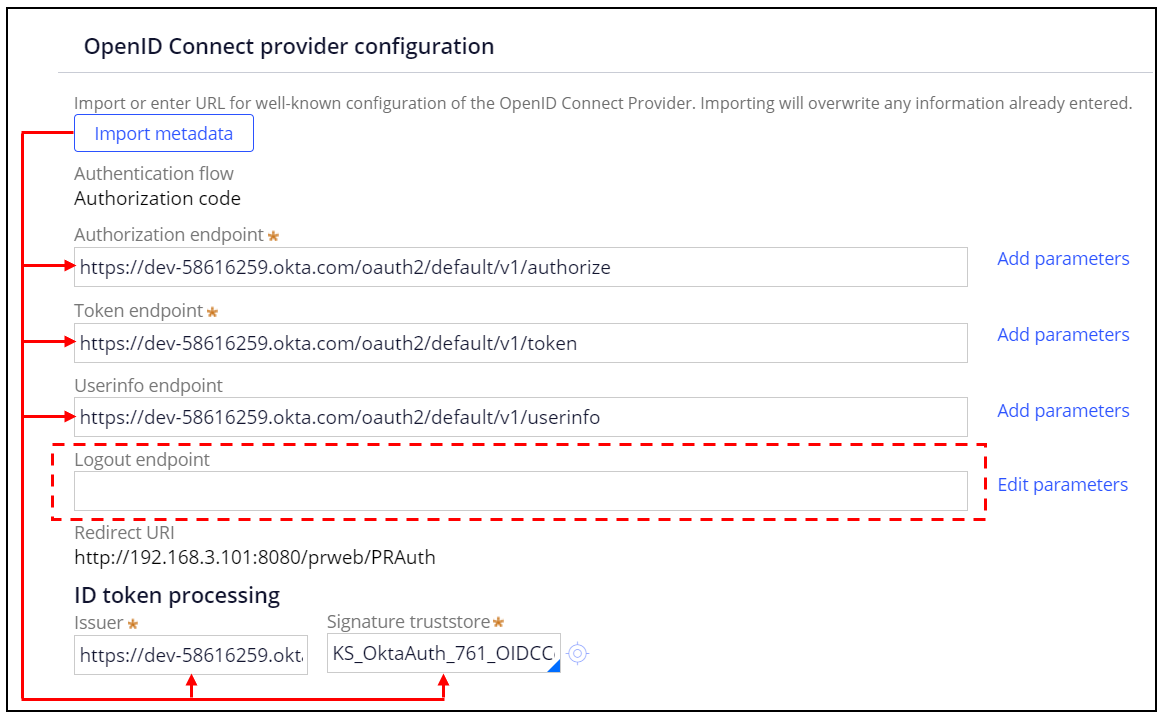
3. Resolution
In order to terminate the session, you can either clear browser cached data or wait for OP's session lifetime (in Okta, 2 hours by default). If you want the system to terminate it automatically when user logs out, you need to configure logout endpoint. We tried three approaches for post redirect URI and I will explain one by one.
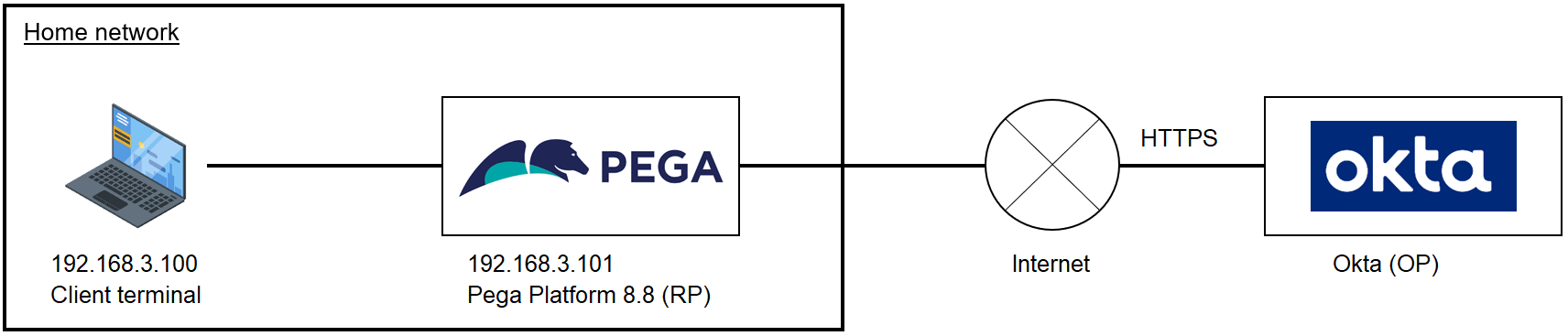
FYI, below is the node structure in this PoC. Replace Pega IP address with yours. If you are on multiple Pega nodes environment (including Pega Cloud), you should use load balancer address.
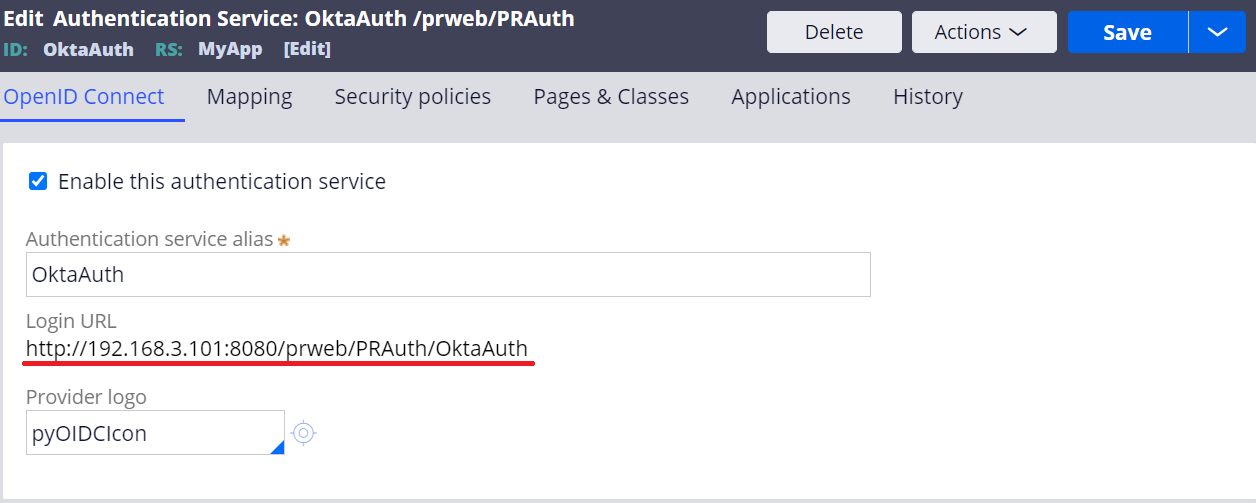
3-1. OIDC log in URL for post redirect URI
1. In the Authentication Service rule, copy other endpoint and modify the last part to logout as below.
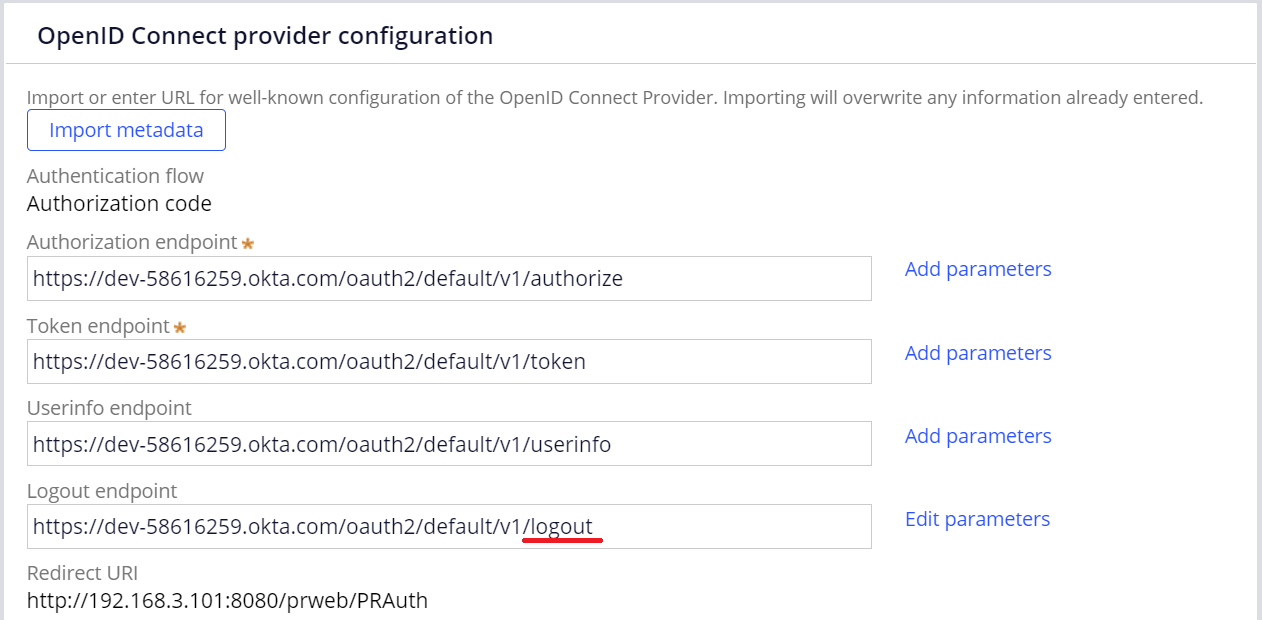
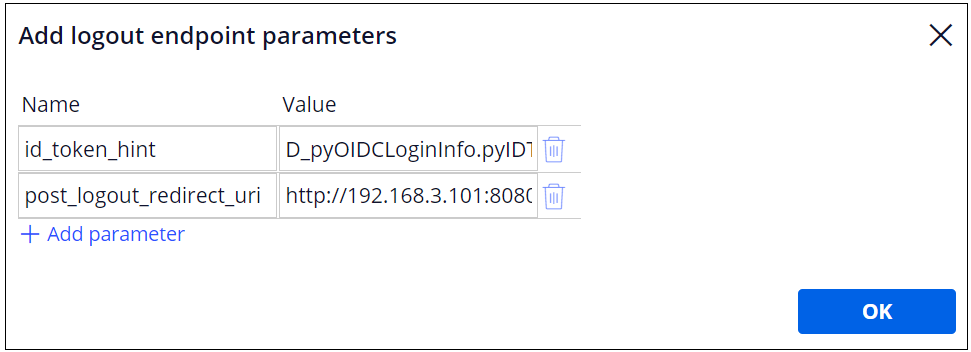
2. Click "Edit parameters" link and add two parameters as below. This is Okta specific and it may be different per OIDC software.
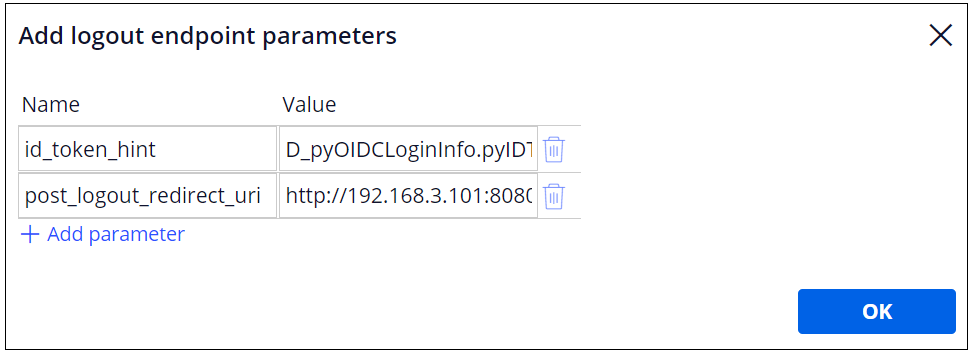
| No | Name | Value |
|---|---|---|
| 1 | id_token_hint | D_pyOIDCLoginInfo.pyIDToken |
| 2 | post_logout_redirect_uri | http:// Proprietary information hidden:8080/prweb/PRAuth/OktaAuth |
For post_logout_redirect_uri, enter your SSO log in URL (shown below).
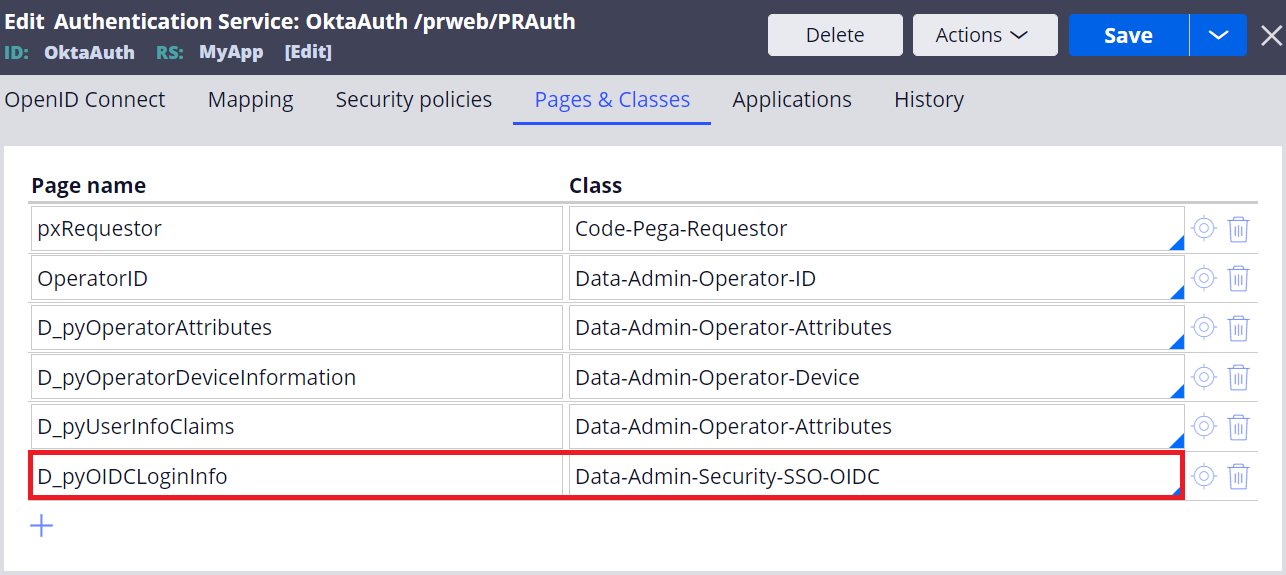
Also, declare Data-Admin-Security-SSO-OIDC class for D_pyOIDCLoginInfo page in Pages & Classes.
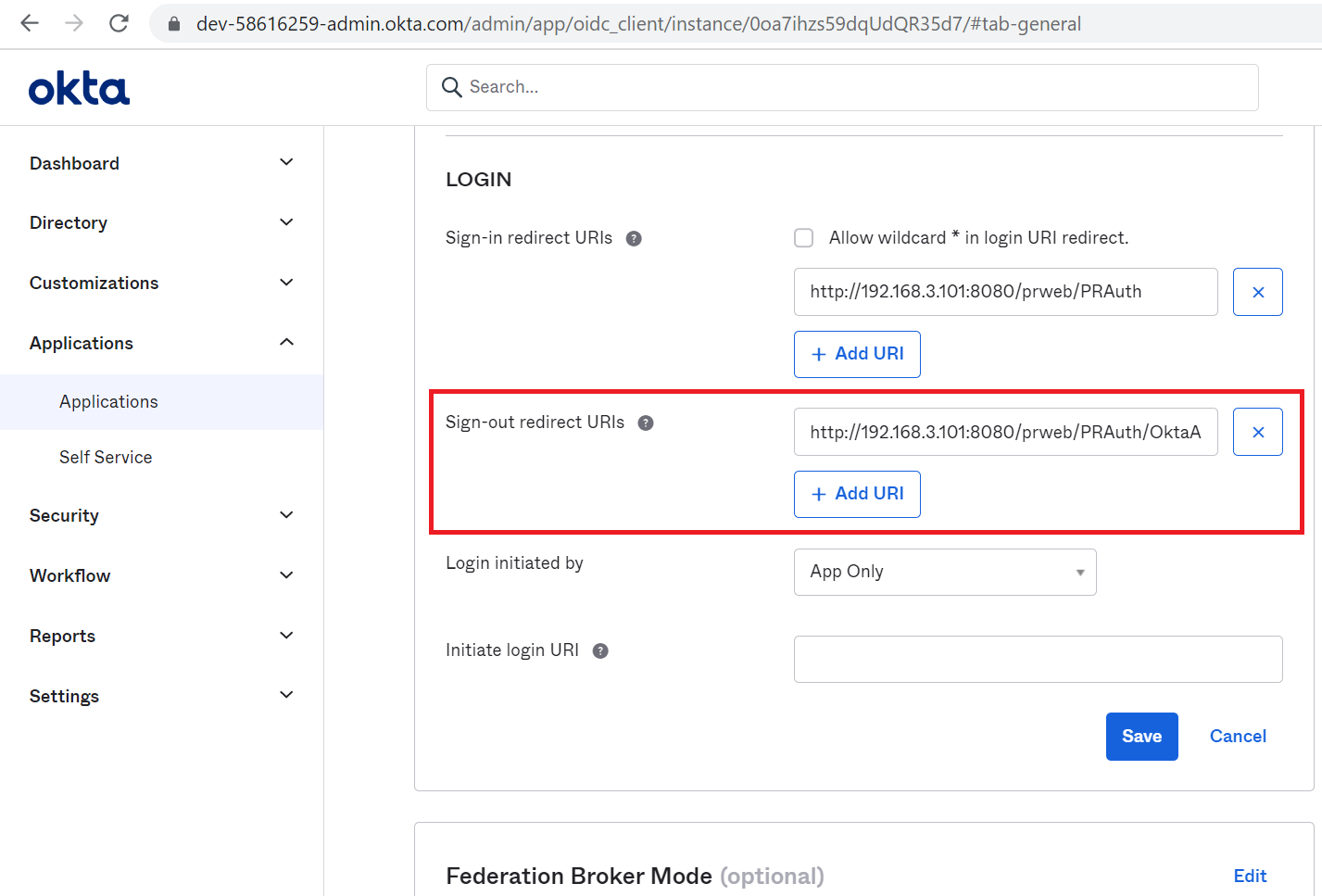
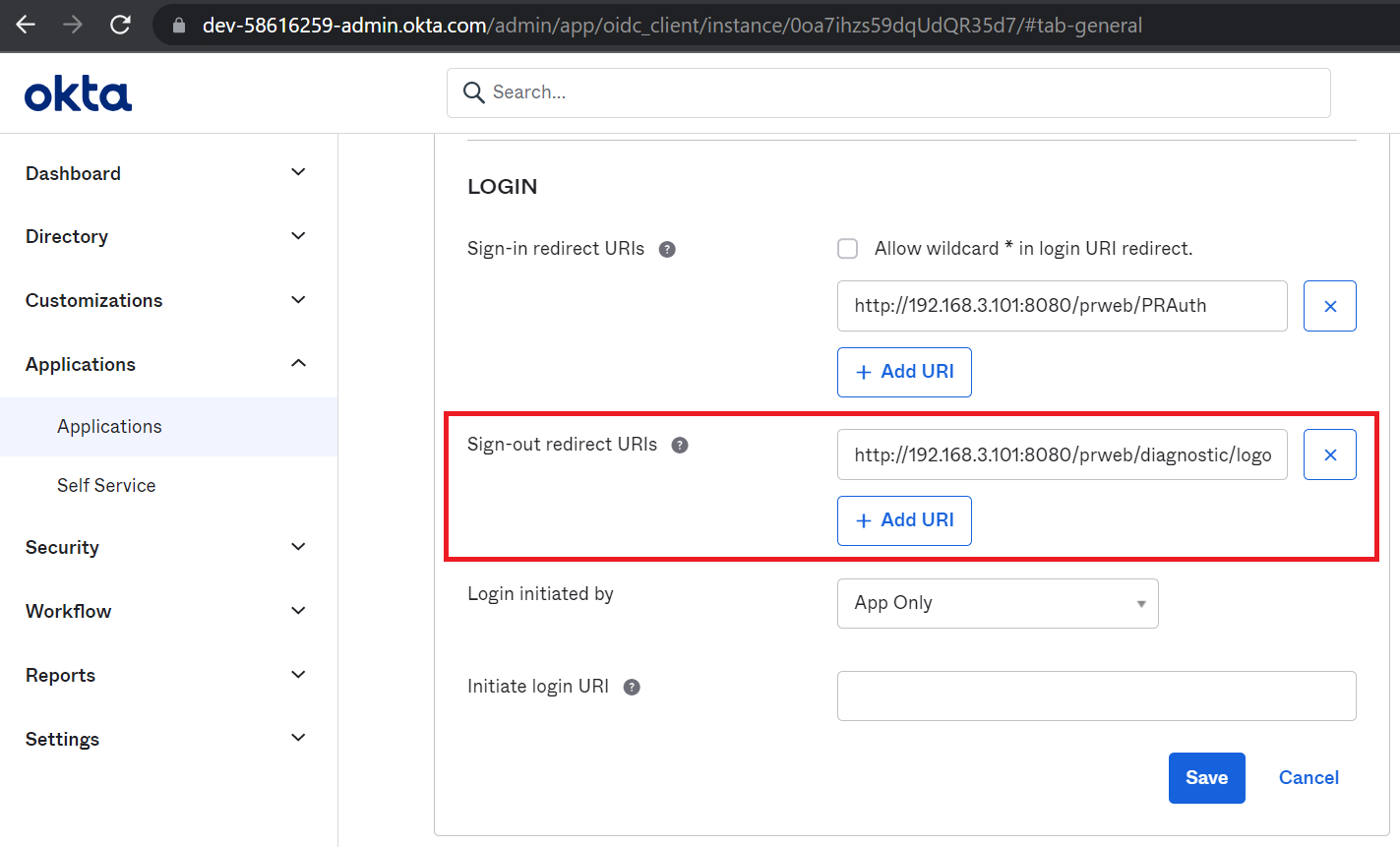
3. The same URL has to be also registered at "Sign-out redirect URIs" in Okta.
4. That's it and now you can test. When you log out, system redirects to Okta for re-authentication. This proves the OIDC session is successfully terminated.

3-2. PRAuth for post redirect URI
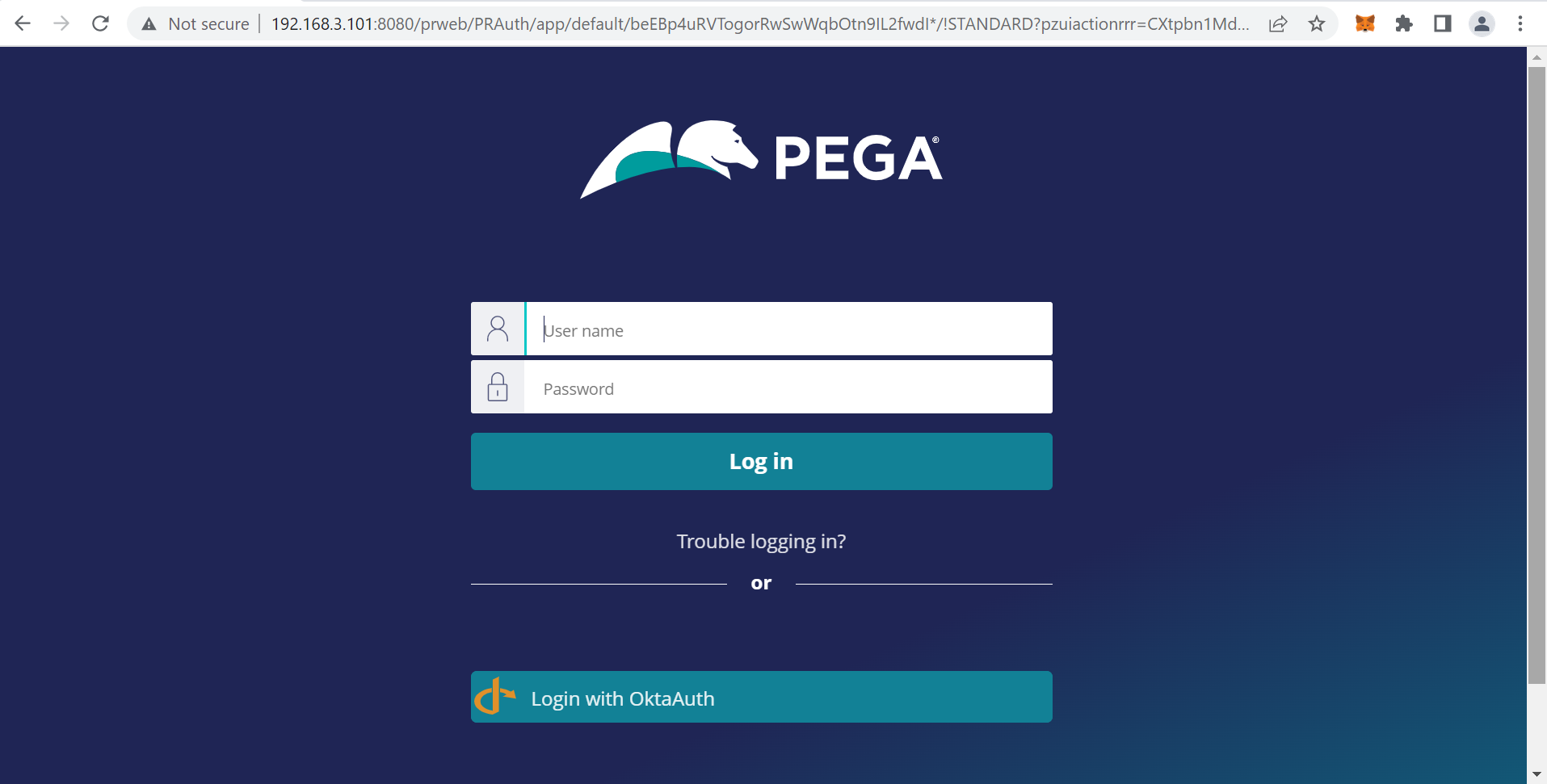
Then we tried PRAuth for post redirect URI. I will only explain the difference from 3-1. Set http:// Proprietary information hidden:8080/prweb/PRAuth for post_logout_redirect_uri, and do the same steps as 3-1 for the rest of configuration. This URL has to be also registered at "Sign-out redirect URIs" in Okta.
That's it and now you can test. When you log out, system shows Pega's PRAuth screen as below. If user clicks on "Login with OktaAuth" at the bottom, he will be redirected to Okta's log in screen where he has to enter Okta credentails for re-authentication.
3-3. Custom JSP for post redirect URI
Since displaying Pega's log out screen is not possible in the current version of Pega Platform, we came up with a workaround. We created and deployed a custom JSP file.
1. Create a logout screen. Screen layout can be your own design. File extension can be either HTML or JSP. In this example, I copied Pega's logout screen source by "View page source" (if you take this approach, use Firefox. We initially tried Chrome / Edge but it didn't work because of different browser interpretation). Save the source code and name it logoff.jsp.
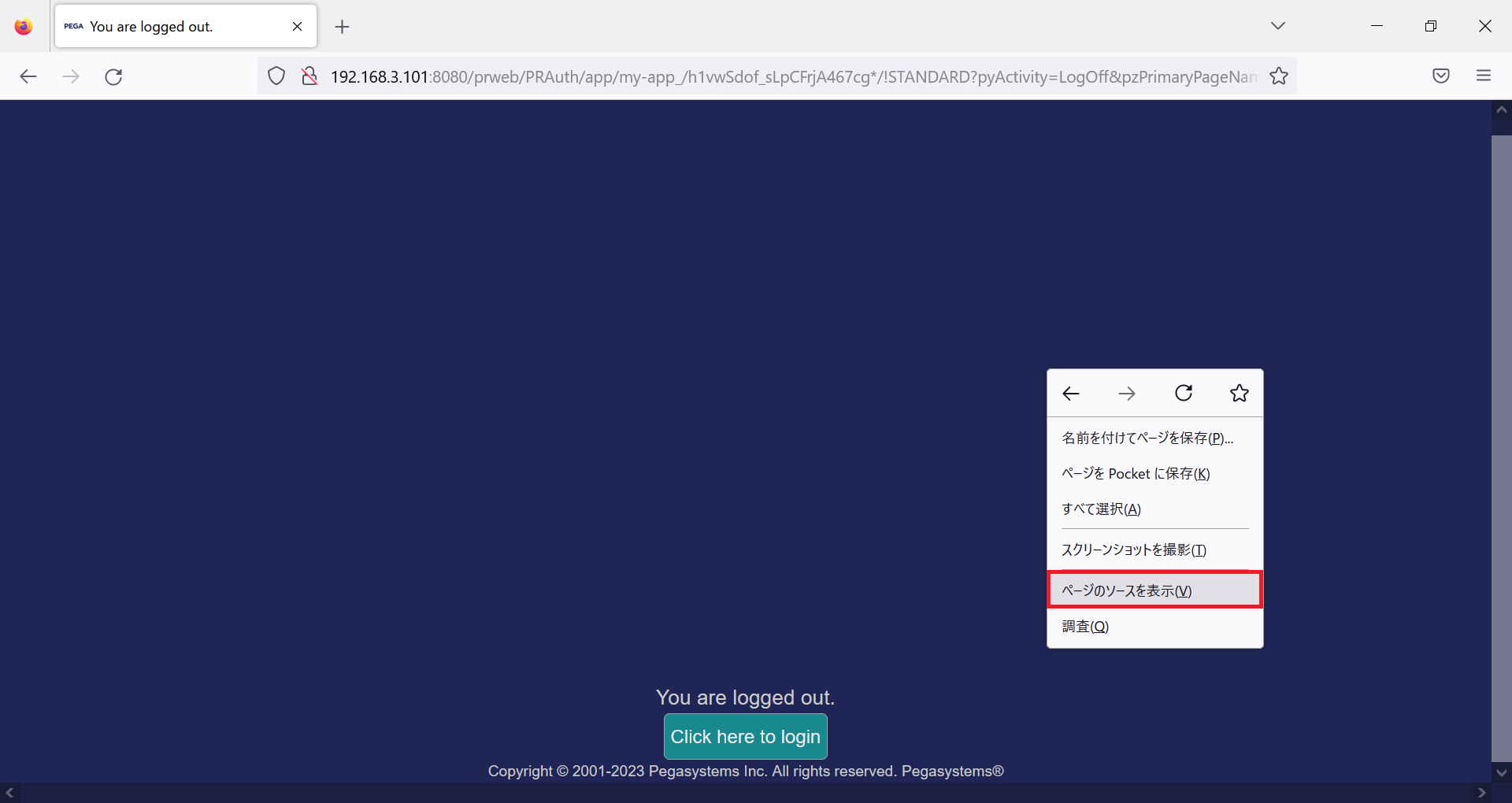
2. Place logoff.jsp file at any temporary directory.
3. Also, copy the following two files to the same temporary directory.
- web.xml from %CATALINA_HOME%\webapps\prweb\WEB-INF
- prweb.war from %CATALINA_HOME%\webapps
4. Open web.xml and add a servlet and servlet-mapping element.
<servlet>
<servlet-name>logoffJSP</servlet-name>
<jsp-file>/diagnostic/logoff.jsp</jsp-file>
</servlet>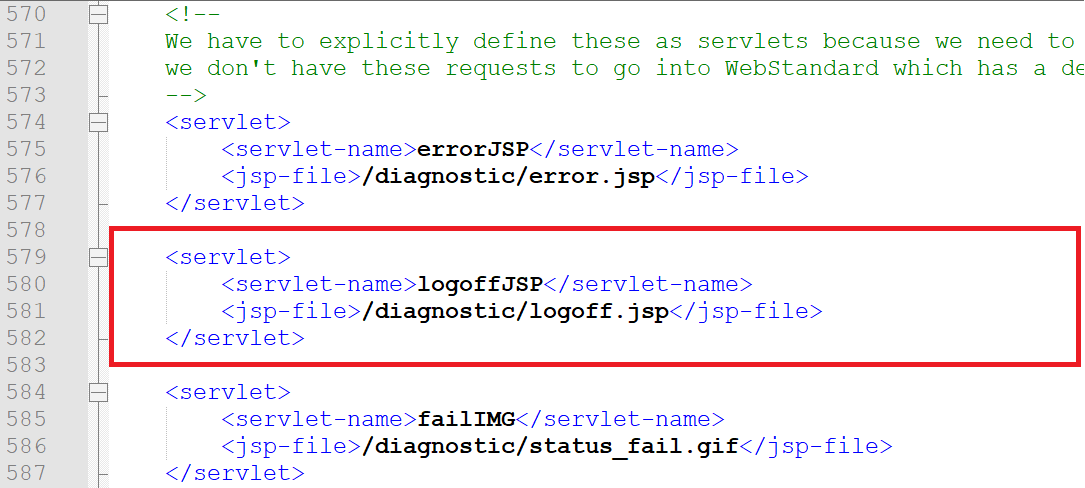
<servlet-mapping>
<servlet-name>logoffJSP</servlet-name>
<url-pattern>/diagnostic/logoff.jsp</url-pattern>
</servlet-mapping>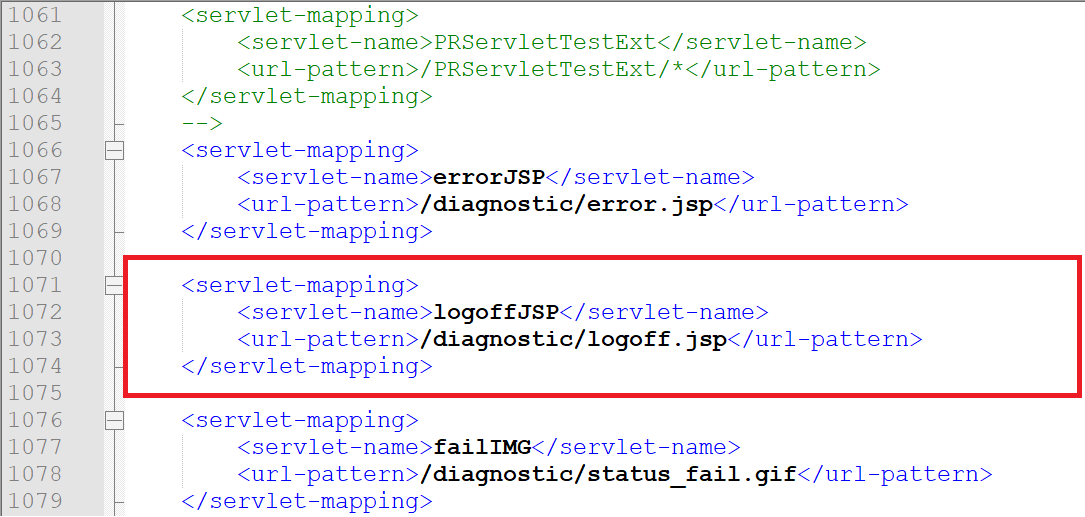
5. Now we need to include these two files into prweb.war. In this example, I used 7-Zip tool. Right-click prweb.war and open it by 7-Zip.
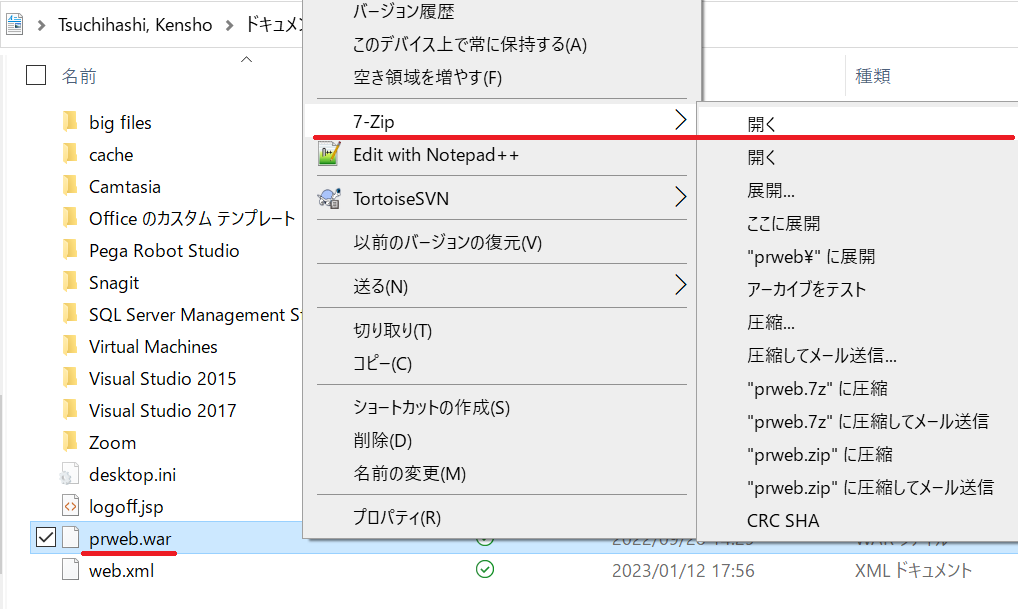
6. Drag & drop two files under the following directory.
- logoff.jsp => prweb.war\diagnostic\
- web.xml => prweb.war\WEB-INF\
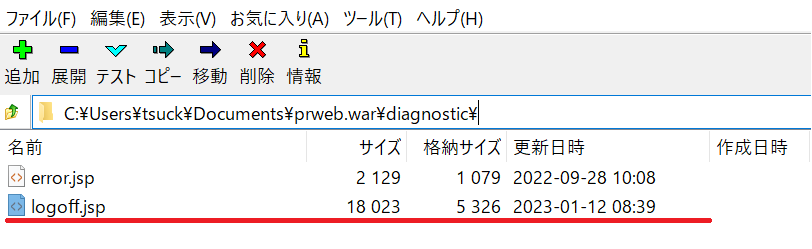
7. Repackaging is done. Stop Tomcat and delete prweb directory & prweb.war file from %CATALINA_HOME%\webapps directory. Place the new prweb.war and restart Tomcat.
8. Tomcat will extract files from prweb.war. Once startup process is completed, make sure logoff.jsp is copied under diagnostic directory, and web.xml is updated.
9. Redeployment is completed. Now open Authentication Service rule and enter http:// Proprietary information hidden:8080/prweb/diagnostic/logoff.jsp for the post_logout_redirect_uri parameter. Logout endpoint and two parameter name are the same as 3-1 or 3-2.
| No | Name | Value |
|---|---|---|
| 1 | id_token_hint | D_pyOIDCLoginInfo.pyIDToken |
| 2 | post_logout_redirect_uri | http:// Proprietary information hidden:8080/prweb/diagnostic/logoff.jsp |
10. The same URL has to be also registered at "Sign-out redirect URIs" in Okta.
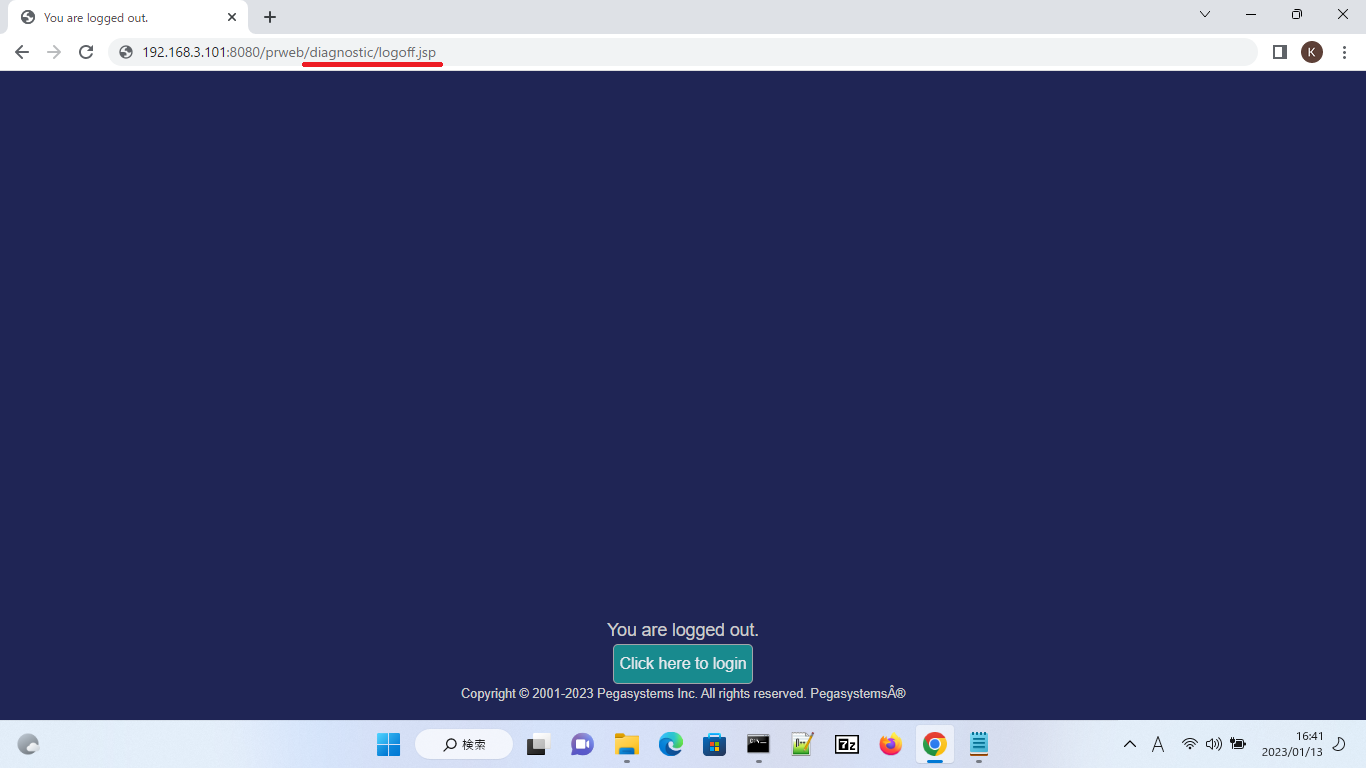
11. That’s it and now you can test. When you log out, system displays your custom JSP / HTML file deployed on Tomcat.
4. Comments
My customer simply wanted to display Pega's logout screen just like when you don't specify logout endpoint in Authentication Service, so we took 3-3 approach. However, this approach is outside of Pega and it is hard to maintain. I've raised an FDBK-95804 for enhancement.
* Note
I have also uploaded a document about how to build OpenID Connect SSO with Okta in a separate post. Please see https://support.pega.com/discussion/how-build-sso-oidc-openid-connect.
Hope this helps.
Thanks,
